Wi-Fi Wi-Fi Wi-Fi Wi-Fi SAS SAS-2 Wi-Fi i
|
|
|
- るるみ とべ
- 7 years ago
- Views:
Transcription
1 26 A Study on Secure Remote Control Methods
2 Wi-Fi Wi-Fi Wi-Fi Wi-Fi SAS SAS-2 Wi-Fi i
3 Abstract A Study on Secure Remote Control Methods SHINGAI, Tatsuro In recent years, communication carriers provides public Wi-Fi services in train stations, airports, the city.this service if you are in possession of the terminal corresponding to the standard of Wi-Fi, you can be utilized.however, sometimes it is provided in a non password in such public Wi-Fi service.in such a case, there is a risk of eavesdropping the communication content from the malicious third party. To solve this problem, there is a remote control.however, the existing products, continue to use a single encryption key. Therefore, it is not maintained confidentiality of communication contents to be eavesdropping key. In this paper, I proposed a method to change the encryption key at regular time intervals and went the application development of applying the proposed method.as a result, In a network that does not safety is secured, it has become possible higher than the existing products confidential communication. key words Remote-Control SAS SAS-2 Wi-Fi One-time password Secure ii
4 VPN Diffie-Hellman Difiie-Hellman RSA RSA SAS SAS iii
5 AuthenticationP hase RemoteControlP hase iv
6 Diffie-Hellman RSA SAS SAS AuthenticationP hase RemoteControlP hase Server Client Server Server Client v
7 vi
8 vii
9 1 1.1 Wi-Fi [1] Wi-Fi LAN Wi-Fi [2] VPN VPN 1
10 1.2 RSA AES RSA AES 1.2 Diffie-Hellman RSA SAS-2 2
11 [3] 2.1 Wi-Fi 3
12 VPN VPN VPN VPN VPN VPN VPN VPN 2.3 Wi-Fi 2.2 4
13 RSA AES 2.3 5
14 2.4 6
15 3 Diffie-Hellman [4] RSA SAS-2 [5] 3.1 Diffie-Hellman Diffie-Hellman Diffie-Hellman X Y 7
16 3.1 Diffie-Hellman p a Z p a X a Y b X b Y K mod Difiie-Hellman Diffie-Hellman a p X Y X Y a X a Y 0 p X b X Y Y b Y X 3.1 Diffie-Hellman b Y = a a Y mod p 8
17 3.1 Diffie-Hellman X a X b Y K K = (b Y ) a X mod p Y a Y b x K K = (b X ) a Y mod p X Y K K = (a a X a Y mod p) b X b Y b X = a a X mod p b Y = a a Y mod p K = (a a X a Y mod p) K X Y Diffie-Hellman a X a Y Diffie-Hellman Man-in-the-middle Attack 9
18 3.2 RSA 3.2 RSA RSA Diffie-Hellman RSA X Y e p q n p Q n a c m z / RSA RSA X 10
19 3.2 RSA X X e p q n n a n a e 3.2 Y n a Y m m n a c X 3.2 RSA c = m e mod n a c X m m = c 1/e mod (p 1)(q 1) mod pq 11
20 3.3 SAS-2 c z e (z ) e n a n a z e c m X Y 3.3 SAS-2 SAS-2 (Replya Attack) (Man-in-the-middle Attack) SAS-2 User Server User ID User S X F H H(x) x i 12
21 3.3 SAS-2 N i i SAS-2 SAS SAS-2 ID S N i ID S N i A = X(ID S N 1 ) ID A ID A
22 3.3 SAS SAS-2 ID S N i A = X(ID S N i ) N i+1 C = X(ID S N i+1 ) F (C) = F (ID C) C F (C) N i+1 α = C (F (C) + A) β = F (C) A ID α β β A F (C) = β A F (C) F (ID C) A C γ = H(ID F (C)) γ H(ID F (C)) γ 14
23 3.3 SAS-2 SAS-2 (i + 1) α E (F (E) + C) β F (E) C ID α x (F (E) + C) β F (x) C ID i SAS-2 15
24 4 Client Server A SAS-2 Ev D, X, F H(x) x i N i i I Server M k I e I M k E ve Ev M k + 16
25 Wi-Fi 4.1 [6] SAS SAS-2 DH RSA or bit 3856 bit 2400 bit Client Server Server Client
26 Client Server AuthenticationP hase RemoteControlP hase Close AuthenticationP hase 4.3 AuthenticationP hase AuthenticationP hase Client Server Client Server A Client Client N i N i C C F (C) C F (C) α β α β Server A M k 18
27 AuthenticationP hase Server Server Client α β A F (C) C C C M k AuthenticationP hase RemoteControlP hase 4.4 RemoteControlP hase RemoteControlP hase E v I RemoteControlP hase AuthenticationP hase Client 19
28 RemoteControlP hase 20
29 4.4 Server C M k Client Client N i N i G G F (G) G F (G) α β E v M k E v E ve E ve α β Server Server Client α β C F (G) G G M k E ve E v E v Server I I M k I e I e Client G Server Client Server I e M k I G Client RemoteControlP hase 4.4 Server 21
30 4.4 Wi-Fi SAS-2 [7] 22
31 5 Client Server 5.1 CPU : Core i5(2.2ghz) : 4GB 23
32 5.2 SAS-2 JAVA AES128bit AES DES 3DES AES Client Server Server Server Server Client Client Client Client Server Client Server 5.2 Socket T CP 24
33 Remote_Client_SAS.java Remote_Server_SAS.java Remote_Client_SAS.java Client Remote_Server_SAS.java Server Server Remote_Server_SAS ( 5.3) 2. Server IP Remote_Client_SAS ( 5.4) 25
34 5.2 実装したアプリケーション 図 5.3 Server プログラム起動 図 Client プログラム起動 実行を行うと 遠隔操作を行う画面が立ち上がる (図 5.5) 画面が立ち上がると Client は AuthenticationP hase に移る (図 5.6) 認証が完了したら Client は操作情報を Server に送信する (図 5.7) Server は操作情報をもとに操作を行い その状態をスクリーンキャプチャし暗号化し て Client に送信する (図 5.8) 7. Client で受け取った暗号化されたデータを復元し 画像データを表示する (図 5.9) 26
35 5.2 実装したアプリケーション 図 5.5 操作画面起動 図 5.6 認証 図 5.7 Server が受信した操作情報 27
36 5.3 利便性の評価 5.3 図 5.8 Server のキャプチャ画像 図 5.9 Client プログラムに表示 利便性の評価 本研究における提案方式を実装して 利便性の評価について述べる 図 5.10 に示す ユー ザが操作情報を入力し Server が処理を行い Client に画像データを送信して Client で 画像の表示を行うまでの応答時間を計測する このサイクルを 1000 回行い平均値 (ms) を 算出する これにより 反応待ちの時間と人間心理の関係について評価を行う 実験環境 実験を行うパソコンのスペックを以下に示す CPU : Core i5(2.2ghz) 28
37 : 4GB Client Server Client Server Client Server ms 96ms 121ms Client 29
38 Server ms 140ms 178ms [8] 5.1 (ms) 100ms 1000ms 10000ms 10000ms 121ms 178ms 100ms 30
39 5.3 31
40 6 Wi-Fi 121ms 178ms Client Server Server Server Client Wi-Fi Wi-Fi 32
41 33
42 [1] 2013 LAN ICT 2013 [2] LAN [3] 2007 [4] W.Diffie and M.E.Hellman New Directions in Cryptography IEEE Transactions on Information Theory vol.it-22 No.6 pp Nov 1976 [5] T.Tsuji and A.Shimizu Simple and secure password authentication protocol ver.2(sas-2) IEICE Technical Reports OIS [6] VoIP 2009 [7] SAS 2013 [8] Jakob Nielsen Response Times:The 3 Important Limits 1993 [9] BP
21 Key Exchange method for portable terminal with direct input by user
 21 Key Exchange method for portable terminal with direct input by user 1110251 2011 3 17 Diffie-Hellman,..,,,,.,, 2.,.,..,,.,, Diffie-Hellman, i Abstract Key Exchange method for portable terminal with
21 Key Exchange method for portable terminal with direct input by user 1110251 2011 3 17 Diffie-Hellman,..,,,,.,, 2.,.,..,,.,, Diffie-Hellman, i Abstract Key Exchange method for portable terminal with
Web Basic Web SAS-2 Web SAS-2 i
 19 Development of moving image delivery system for elementary school 1080337 2008 3 10 Web Basic Web SAS-2 Web SAS-2 i Abstract Development of moving image delivery system for elementary school Ayuko INOUE
19 Development of moving image delivery system for elementary school 1080337 2008 3 10 Web Basic Web SAS-2 Web SAS-2 i Abstract Development of moving image delivery system for elementary school Ayuko INOUE
 28 SAS-X Proposal of Multi Device Authenticable Password Management System using SAS-X 1195074 2017 2 3 SAS-X Web ID/ ID/ Web SAS-2 SAS-X i Abstract Proposal of Multi Device Authenticable Password Management
28 SAS-X Proposal of Multi Device Authenticable Password Management System using SAS-X 1195074 2017 2 3 SAS-X Web ID/ ID/ Web SAS-2 SAS-X i Abstract Proposal of Multi Device Authenticable Password Management
i
 21 Fault-Toleranted Authentication Data Distribution Protocol for Autonomous Distributed Networks 1125153 2010 3 2 i Abstract Fault-Toleranted Authentication Data Distribution Protocol for Autonomous Distributed
21 Fault-Toleranted Authentication Data Distribution Protocol for Autonomous Distributed Networks 1125153 2010 3 2 i Abstract Fault-Toleranted Authentication Data Distribution Protocol for Autonomous Distributed
LAN LAN LAN LAN LAN LAN,, i
 22 A secure wireless communication system using virtualization technologies 1115139 2011 3 4 LAN LAN LAN LAN LAN LAN,, i Abstract A secure wireless communication system using virtualization technologies
22 A secure wireless communication system using virtualization technologies 1115139 2011 3 4 LAN LAN LAN LAN LAN LAN,, i Abstract A secure wireless communication system using virtualization technologies
21 VoIP An encrypted VoIP communication system for mobile telephones
 21 VoIP An encrypted VoIP communication system for mobile telephones 1095702 2010 3 4 VoIP, IP., IP, VoIP(Voice over Internet Protocol)., VoIP,., VoIP over SSL(VoIPs), VoIPs.,,.,, VoIP., LAN VoIP. LAN
21 VoIP An encrypted VoIP communication system for mobile telephones 1095702 2010 3 4 VoIP, IP., IP, VoIP(Voice over Internet Protocol)., VoIP,., VoIP over SSL(VoIPs), VoIPs.,,.,, VoIP., LAN VoIP. LAN
Web Web ID Web 16 Web Web i
 24 Web Proposal of Web Application Password Operations Management System 1130343 2013 3 1 Web Web ID Web 16 Web Web i Abstract Proposal of Web Application Password Operations Management System Tatsuro
24 Web Proposal of Web Application Password Operations Management System 1130343 2013 3 1 Web Web ID Web 16 Web Web i Abstract Proposal of Web Application Password Operations Management System Tatsuro
Web Web Web Web i
 28 Research of password manager using pattern lock and user certificate 1170369 2017 2 28 Web Web Web Web i Abstract Research of password manager using pattern lock and user certificate Takuya Mimoto In
28 Research of password manager using pattern lock and user certificate 1170369 2017 2 28 Web Web Web Web i Abstract Research of password manager using pattern lock and user certificate Takuya Mimoto In
25 About what prevent spoofing of misusing a session information
 25 About what prevent spoofing of misusing a session information 1140349 2014 2 28 Web Web [1]. [2] SAS-2(Simple And Secure password authentication protocol, ver.2)[3] SAS-2 i Abstract About what prevent
25 About what prevent spoofing of misusing a session information 1140349 2014 2 28 Web Web [1]. [2] SAS-2(Simple And Secure password authentication protocol, ver.2)[3] SAS-2 i Abstract About what prevent
7,, i
 23 Research of the authentication method on the two dimensional code 1145111 2012 2 13 7,, i Abstract Research of the authentication method on the two dimensional code Karita Koichiro Recently, the two
23 Research of the authentication method on the two dimensional code 1145111 2012 2 13 7,, i Abstract Research of the authentication method on the two dimensional code Karita Koichiro Recently, the two
,,,,., C Java,,.,,.,., ,,.,, i
 24 Development of the programming s learning tool for children be derived from maze 1130353 2013 3 1 ,,,,., C Java,,.,,.,., 1 6 1 2.,,.,, i Abstract Development of the programming s learning tool for children
24 Development of the programming s learning tool for children be derived from maze 1130353 2013 3 1 ,,,,., C Java,,.,,.,., 1 6 1 2.,,.,, i Abstract Development of the programming s learning tool for children
SOM SOM(Self-Organizing Maps) SOM SOM SOM SOM SOM SOM i
 20 SOM Development of Syllabus Vsualization System using Spherical Self-Organizing Maps 1090366 2009 3 5 SOM SOM(Self-Organizing Maps) SOM SOM SOM SOM SOM SOM i Abstract Development of Syllabus Vsualization
20 SOM Development of Syllabus Vsualization System using Spherical Self-Organizing Maps 1090366 2009 3 5 SOM SOM(Self-Organizing Maps) SOM SOM SOM SOM SOM SOM i Abstract Development of Syllabus Vsualization
Virtual Window System Virtual Window System Virtual Window System Virtual Window System Virtual Window System Virtual Window System Social Networking
 23 An attribute expression of the virtual window system communicators 1120265 2012 3 1 Virtual Window System Virtual Window System Virtual Window System Virtual Window System Virtual Window System Virtual
23 An attribute expression of the virtual window system communicators 1120265 2012 3 1 Virtual Window System Virtual Window System Virtual Window System Virtual Window System Virtual Window System Virtual
21 e-learning Development of Real-time Learner Detection System for e-learning
 21 e-learning Development of Real-time Learner Detection System for e-learning 1100349 2010 3 1 e-learning WBT (Web Based training) e-learning LMS (Learning Management System) LMS WBT e-learning e-learning
21 e-learning Development of Real-time Learner Detection System for e-learning 1100349 2010 3 1 e-learning WBT (Web Based training) e-learning LMS (Learning Management System) LMS WBT e-learning e-learning
Web Web Web Web Web, i
 22 Web Research of a Web search support system based on individual sensitivity 1135117 2011 2 14 Web Web Web Web Web, i Abstract Research of a Web search support system based on individual sensitivity
22 Web Research of a Web search support system based on individual sensitivity 1135117 2011 2 14 Web Web Web Web Web, i Abstract Research of a Web search support system based on individual sensitivity
( )
 NAIST-IS-MT0851100 2010 2 4 ( ) CR CR CR 1980 90 CR Kerberos SSH CR CR CR CR CR CR,,, ID, NAIST-IS- MT0851100, 2010 2 4. i On the Key Management Policy of Challenge Response Authentication Schemes Toshiya
NAIST-IS-MT0851100 2010 2 4 ( ) CR CR CR 1980 90 CR Kerberos SSH CR CR CR CR CR CR,,, ID, NAIST-IS- MT0851100, 2010 2 4. i On the Key Management Policy of Challenge Response Authentication Schemes Toshiya
23 Study on Generation of Sudoku Problems with Fewer Clues
 23 Study on Generation of Sudoku Problems with Fewer Clues 1120254 2012 3 1 9 9 21 18 i Abstract Study on Generation of Sudoku Problems with Fewer Clues Norimasa NASU Sudoku is puzzle a kind of pencil
23 Study on Generation of Sudoku Problems with Fewer Clues 1120254 2012 3 1 9 9 21 18 i Abstract Study on Generation of Sudoku Problems with Fewer Clues Norimasa NASU Sudoku is puzzle a kind of pencil
,,.,,., II,,,.,,.,.,,,.,,,.,, II i
 12 Load Dispersion Methods in Thin Client Systems 1010405 2001 2 5 ,,.,,., II,,,.,,.,.,,,.,,,.,, II i Abstract Load Dispersion Methods in Thin Client Systems Noritaka TAKEUCHI Server Based Computing by
12 Load Dispersion Methods in Thin Client Systems 1010405 2001 2 5 ,,.,,., II,,,.,,.,.,,,.,,,.,, II i Abstract Load Dispersion Methods in Thin Client Systems Noritaka TAKEUCHI Server Based Computing by
58 10
 57 Multi-channel MAC Protocol with Multi-busytone in Ad-hoc Networks Masatoshi Fukushima*, Ushio Yamamoto* and Yoshikuni Onozato* Abstract Multi-channel MAC protocols for wireless ad hoc networks have
57 Multi-channel MAC Protocol with Multi-busytone in Ad-hoc Networks Masatoshi Fukushima*, Ushio Yamamoto* and Yoshikuni Onozato* Abstract Multi-channel MAC protocols for wireless ad hoc networks have
 i ii iii iv v vi vii ( ー ー ) ( ) ( ) ( ) ( ) ー ( ) ( ) ー ー ( ) ( ) ( ) ( ) ( ) 13 202 24122783 3622316 (1) (2) (3) (4) 2483 (1) (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) 11 11 2483 13
i ii iii iv v vi vii ( ー ー ) ( ) ( ) ( ) ( ) ー ( ) ( ) ー ー ( ) ( ) ( ) ( ) ( ) 13 202 24122783 3622316 (1) (2) (3) (4) 2483 (1) (2) (3) (4) (5) (6) (7) (8) (9) (10) (11) 11 11 2483 13
paper.dvi
 28 Confined Decoding System for Medical Data Distributed by Secret Sharing Scheme and Its Security Evaluation 1195046 2017 3 6 DMAT i Abstract Confined Decoding System for Medical Data Distributed by Secret
28 Confined Decoding System for Medical Data Distributed by Secret Sharing Scheme and Its Security Evaluation 1195046 2017 3 6 DMAT i Abstract Confined Decoding System for Medical Data Distributed by Secret
P2P Web Proxy P2P Web Proxy P2P P2P Web Proxy P2P Web Proxy Web P2P WebProxy i
 27 Verification of the usefulness of the data distribution method by browser cache sharing 1160285 2016 2 26 P2P Web Proxy P2P Web Proxy P2P P2P Web Proxy P2P Web Proxy Web P2P WebProxy i Abstract Verification
27 Verification of the usefulness of the data distribution method by browser cache sharing 1160285 2016 2 26 P2P Web Proxy P2P Web Proxy P2P P2P Web Proxy P2P Web Proxy Web P2P WebProxy i Abstract Verification
29 jjencode JavaScript
 Kochi University of Technology Aca Title jjencode で難読化された JavaScript の検知 Author(s) 中村, 弘亮 Citation Date of 2018-03 issue URL http://hdl.handle.net/10173/1975 Rights Text version author Kochi, JAPAN http://kutarr.lib.kochi-tech.ac.jp/dspa
Kochi University of Technology Aca Title jjencode で難読化された JavaScript の検知 Author(s) 中村, 弘亮 Citation Date of 2018-03 issue URL http://hdl.handle.net/10173/1975 Rights Text version author Kochi, JAPAN http://kutarr.lib.kochi-tech.ac.jp/dspa
28 Docker Design and Implementation of Program Evaluation System Using Docker Virtualized Environment
 28 Docker Design and Implementation of Program Evaluation System Using Docker Virtualized Environment 1170288 2017 2 28 Docker,.,,.,,.,,.,. Docker.,..,., Web, Web.,.,.,, CPU,,. i ., OS..,, OS, VirtualBox,.,
28 Docker Design and Implementation of Program Evaluation System Using Docker Virtualized Environment 1170288 2017 2 28 Docker,.,,.,,.,,.,. Docker.,..,., Web, Web.,.,.,, CPU,,. i ., OS..,, OS, VirtualBox,.,
 17 Multiple video streams control for the synchronous delivery and playback 1085404 2006 3 10 Web IP 1 1 1 3,,, i Abstract Multiple video streams control for the synchronous delivery and playback Yoshiyuki
17 Multiple video streams control for the synchronous delivery and playback 1085404 2006 3 10 Web IP 1 1 1 3,,, i Abstract Multiple video streams control for the synchronous delivery and playback Yoshiyuki
DTN DTN DTN DTN i
 28 DTN Proposal of the Aggregation Message Ferrying for Evacuee s Data Delivery in DTN Environment 1170302 2017 2 28 DTN DTN DTN DTN i Abstract Proposal of the Aggregation Message Ferrying for Evacuee
28 DTN Proposal of the Aggregation Message Ferrying for Evacuee s Data Delivery in DTN Environment 1170302 2017 2 28 DTN DTN DTN DTN i Abstract Proposal of the Aggregation Message Ferrying for Evacuee
, IT.,.,..,.. i
 25 To construct the system that promote a interactive method as a knowledge acquisition 1140317 2014 2 28 , IT.,.,..,.. i Abstract To construct the system that promote a interactive method as a knowledge
25 To construct the system that promote a interactive method as a knowledge acquisition 1140317 2014 2 28 , IT.,.,..,.. i Abstract To construct the system that promote a interactive method as a knowledge
IT i
 27 The automatic extract of know-how search tag using a thesaurus 1160374 2016 2 26 IT i Abstract The automatic extract of know-how search tag using a thesaurus In recent years, a number of organizational
27 The automatic extract of know-how search tag using a thesaurus 1160374 2016 2 26 IT i Abstract The automatic extract of know-how search tag using a thesaurus In recent years, a number of organizational
WebRTC P2P Web Proxy P2P Web Proxy WebRTC WebRTC Web, HTTP, WebRTC, P2P i
 26 WebRTC The data distribution system using browser cache sharing and WebRTC 1150361 2015/02/27 WebRTC P2P Web Proxy P2P Web Proxy WebRTC WebRTC Web, HTTP, WebRTC, P2P i Abstract The data distribution
26 WebRTC The data distribution system using browser cache sharing and WebRTC 1150361 2015/02/27 WebRTC P2P Web Proxy P2P Web Proxy WebRTC WebRTC Web, HTTP, WebRTC, P2P i Abstract The data distribution
PC PDA SMTP/POP3 1 POP3 SMTP MUA MUA MUA i
 21 The private mailers synchronization operation for plural terminals 1125083 2010 3 1 PC PDA SMTP/POP3 1 POP3 SMTP MUA MUA MUA i Abstract The private mailers synchronization operation for plural terminals
21 The private mailers synchronization operation for plural terminals 1125083 2010 3 1 PC PDA SMTP/POP3 1 POP3 SMTP MUA MUA MUA i Abstract The private mailers synchronization operation for plural terminals
P2P P2P Winny 3 P2P 15 20 P2P 1 P2P, i
 26 P2P Reduction of search packets by sharing peer information in P2P communication 1175073 2015 2 27 P2P P2P Winny 3 P2P 15 20 P2P 1 P2P, i Abstract Reduction of search packets by sharing peer information
26 P2P Reduction of search packets by sharing peer information in P2P communication 1175073 2015 2 27 P2P P2P Winny 3 P2P 15 20 P2P 1 P2P, i Abstract Reduction of search packets by sharing peer information
IT,, i
 22 Retrieval support system using bookmarks that are shared in an organization 1110250 2011 3 17 IT,, i Abstract Retrieval support system using bookmarks that are shared in an organization Yoshihiko Komaki
22 Retrieval support system using bookmarks that are shared in an organization 1110250 2011 3 17 IT,, i Abstract Retrieval support system using bookmarks that are shared in an organization Yoshihiko Komaki
WebRTC P2P,. Web,. WebRTC. WebRTC, P2P, i
 28 WebRTC Design of multi-platform file sharing system using WebRTC 1170336 2017 2 28 WebRTC P2P,. Web,. WebRTC. WebRTC, P2P, i Abstract Design of multi-platform file sharing system using WebRTC Harumi
28 WebRTC Design of multi-platform file sharing system using WebRTC 1170336 2017 2 28 WebRTC P2P,. Web,. WebRTC. WebRTC, P2P, i Abstract Design of multi-platform file sharing system using WebRTC Harumi
23 The Study of support narrowing down goods on electronic commerce sites
 23 The Study of support narrowing down goods on electronic commerce sites 1120256 2012 3 15 i Abstract The Study of support narrowing down goods on electronic commerce sites Masaki HASHIMURA Recently,
23 The Study of support narrowing down goods on electronic commerce sites 1120256 2012 3 15 i Abstract The Study of support narrowing down goods on electronic commerce sites Masaki HASHIMURA Recently,
ネットワーク化するデジタル情報家電の動向
 In this broadband era, Information Technology has started at a market targeting home consumers, and upon gaining good achievements there would move on to be used in the business and enterprise markets.
In this broadband era, Information Technology has started at a market targeting home consumers, and upon gaining good achievements there would move on to be used in the business and enterprise markets.
Microsoft Word - Win-Outlook.docx
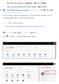 Microsoft Office Outlook での設定方法 (IMAP および POP 編 ) How to set up with Microsoft Office Outlook (IMAP and POP) 0. 事前に https://office365.iii.kyushu-u.ac.jp/login からサインインし 以下の手順で自分の基本アドレスをメモしておいてください Sign
Microsoft Office Outlook での設定方法 (IMAP および POP 編 ) How to set up with Microsoft Office Outlook (IMAP and POP) 0. 事前に https://office365.iii.kyushu-u.ac.jp/login からサインインし 以下の手順で自分の基本アドレスをメモしておいてください Sign
これわかWord2010_第1部_100710.indd
 i 1 1 2 3 6 6 7 8 10 10 11 12 12 12 13 2 15 15 16 17 17 18 19 20 20 21 ii CONTENTS 25 26 26 28 28 29 30 30 31 32 35 35 35 36 37 40 42 44 44 45 46 49 50 50 51 iii 52 52 52 53 55 56 56 57 58 58 60 60 iv
i 1 1 2 3 6 6 7 8 10 10 11 12 12 12 13 2 15 15 16 17 17 18 19 20 20 21 ii CONTENTS 25 26 26 28 28 29 30 30 31 32 35 35 35 36 37 40 42 44 44 45 46 49 50 50 51 iii 52 52 52 53 55 56 56 57 58 58 60 60 iv
パワポカバー入稿用.indd
 i 1 1 2 2 3 3 4 4 4 5 7 8 8 9 9 10 11 13 14 15 16 17 19 ii CONTENTS 2 21 21 22 25 26 32 37 38 39 39 41 41 43 43 43 44 45 46 47 47 49 52 54 56 56 iii 57 59 62 64 64 66 67 68 71 72 72 73 74 74 77 79 81 84
i 1 1 2 2 3 3 4 4 4 5 7 8 8 9 9 10 11 13 14 15 16 17 19 ii CONTENTS 2 21 21 22 25 26 32 37 38 39 39 41 41 43 43 43 44 45 46 47 47 49 52 54 56 56 iii 57 59 62 64 64 66 67 68 71 72 72 73 74 74 77 79 81 84
これでわかるAccess2010
 i 1 1 1 2 2 2 3 4 4 5 6 7 7 9 10 11 12 13 14 15 17 ii CONTENTS 2 19 19 20 23 24 25 25 26 29 29 31 31 33 35 36 36 39 39 41 44 45 46 48 iii 50 50 52 54 55 57 57 59 61 63 64 66 66 67 70 70 73 74 74 77 77
i 1 1 1 2 2 2 3 4 4 5 6 7 7 9 10 11 12 13 14 15 17 ii CONTENTS 2 19 19 20 23 24 25 25 26 29 29 31 31 33 35 36 36 39 39 41 44 45 46 48 iii 50 50 52 54 55 57 57 59 61 63 64 66 66 67 70 70 73 74 74 77 77
n 2 n (Dynamic Programming : DP) (Genetic Algorithm : GA) 2 i
 15 Comparison and Evaluation of Dynamic Programming and Genetic Algorithm for a Knapsack Problem 1040277 2004 2 25 n 2 n (Dynamic Programming : DP) (Genetic Algorithm : GA) 2 i Abstract Comparison and
15 Comparison and Evaluation of Dynamic Programming and Genetic Algorithm for a Knapsack Problem 1040277 2004 2 25 n 2 n (Dynamic Programming : DP) (Genetic Algorithm : GA) 2 i Abstract Comparison and
卒業論文2.dvi
 15 GUI A study on the system to transfer a GUI sub-picture to the enlarging viewer for operational support 1040270 2004 2 27 GUI PC PC GUI Graphical User Interface PC GUI GUI PC GUI PC PC GUI i Abstract
15 GUI A study on the system to transfer a GUI sub-picture to the enlarging viewer for operational support 1040270 2004 2 27 GUI PC PC GUI Graphical User Interface PC GUI GUI PC GUI PC PC GUI i Abstract
28 Horizontal angle correction using straight line detection in an equirectangular image
 28 Horizontal angle correction using straight line detection in an equirectangular image 1170283 2017 3 1 2 i Abstract Horizontal angle correction using straight line detection in an equirectangular image
28 Horizontal angle correction using straight line detection in an equirectangular image 1170283 2017 3 1 2 i Abstract Horizontal angle correction using straight line detection in an equirectangular image
Web ( ) [1] Web Shibboleth SSO Web SSO Web Web Shibboleth SAML IdP(Identity Provider) Web Web (SP:ServiceProvider) ( ) IdP Web Web MRA(Mail Retrieval
![Web ( ) [1] Web Shibboleth SSO Web SSO Web Web Shibboleth SAML IdP(Identity Provider) Web Web (SP:ServiceProvider) ( ) IdP Web Web MRA(Mail Retrieval Web ( ) [1] Web Shibboleth SSO Web SSO Web Web Shibboleth SAML IdP(Identity Provider) Web Web (SP:ServiceProvider) ( ) IdP Web Web MRA(Mail Retrieval](/thumbs/77/76504768.jpg) SAML PAM SSO Web 1,a) 1 1 1 Shibboleth SAML Web IMAPS Web SAML PAM IMAPS SSO Web Shibboleth Web SSO, Shibboleth, SAML, Web, Web-based mail system with SSO authentication through SAML supporting PAM Makoto
SAML PAM SSO Web 1,a) 1 1 1 Shibboleth SAML Web IMAPS Web SAML PAM IMAPS SSO Web Shibboleth Web SSO, Shibboleth, SAML, Web, Web-based mail system with SSO authentication through SAML supporting PAM Makoto
29 Short-time prediction of time series data for binary option trade
 29 Short-time prediction of time series data for binary option trade 1180365 2018 2 28 RSI(Relative Strength Index) 3 USD/JPY 1 2001 1 2 4 10 2017 12 29 17 00 1 high low i Abstract Short-time prediction
29 Short-time prediction of time series data for binary option trade 1180365 2018 2 28 RSI(Relative Strength Index) 3 USD/JPY 1 2001 1 2 4 10 2017 12 29 17 00 1 high low i Abstract Short-time prediction
IPSJ SIG Technical Report PIN(Personal Identification Number) An Examination of Icon-based User Authentication Method for Mobile Terminals Fum
 1 2 1 3 PIN(Personal Identification Number) An Examination of Icon-based User Authentication Method for Mobile Terminals Fumio Sugai, 1 Masami Ikeda, 2 Naonobu Okazaki 1 and Mi RangPark 3 In recent years,
1 2 1 3 PIN(Personal Identification Number) An Examination of Icon-based User Authentication Method for Mobile Terminals Fumio Sugai, 1 Masami Ikeda, 2 Naonobu Okazaki 1 and Mi RangPark 3 In recent years,
1 1 tf-idf tf-idf i
 14 A Method of Article Retrieval Utilizing Characteristics in Newspaper Articles 1055104 2003 1 31 1 1 tf-idf tf-idf i Abstract A Method of Article Retrieval Utilizing Characteristics in Newspaper Articles
14 A Method of Article Retrieval Utilizing Characteristics in Newspaper Articles 1055104 2003 1 31 1 1 tf-idf tf-idf i Abstract A Method of Article Retrieval Utilizing Characteristics in Newspaper Articles
2
 1 2 3 4 5 6 7 8 9 10 I II III 11 IV 12 V 13 VI VII 14 VIII. 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 _ 33 _ 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 VII 51 52 53 54 55 56 57 58 59
1 2 3 4 5 6 7 8 9 10 I II III 11 IV 12 V 13 VI VII 14 VIII. 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 _ 33 _ 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 VII 51 52 53 54 55 56 57 58 59
untitled
 i ii iii iv v 43 43 vi 43 vii T+1 T+2 1 viii 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 a) ( ) b) ( ) 51
i ii iii iv v 43 43 vi 43 vii T+1 T+2 1 viii 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 a) ( ) b) ( ) 51
,,.,.,,.,.,.,.,,.,..,,,, i
 22 A person recognition using color information 1110372 2011 2 13 ,,.,.,,.,.,.,.,,.,..,,,, i Abstract A person recognition using color information Tatsumo HOJI Recently, for the purpose of collection of
22 A person recognition using color information 1110372 2011 2 13 ,,.,.,,.,.,.,.,,.,..,,,, i Abstract A person recognition using color information Tatsumo HOJI Recently, for the purpose of collection of
HP cafe HP of A A B of C C Map on N th Floor coupon A cafe coupon B Poster A Poster A Poster B Poster B Case 1 Show HP of each company on a user scree
 LAN 1 2 3 2 LAN WiFiTag WiFiTag LAN LAN 100% WiFi Tag An Improved Determination Method with Multiple Access Points for Relative Position Estimation Using Wireless LAN Abstract: We have proposed a WiFiTag
LAN 1 2 3 2 LAN WiFiTag WiFiTag LAN LAN 100% WiFi Tag An Improved Determination Method with Multiple Access Points for Relative Position Estimation Using Wireless LAN Abstract: We have proposed a WiFiTag
25 Removal of the fricative sounds that occur in the electronic stethoscope
 25 Removal of the fricative sounds that occur in the electronic stethoscope 1140311 2014 3 7 ,.,.,.,.,.,.,.,,.,.,.,.,,. i Abstract Removal of the fricative sounds that occur in the electronic stethoscope
25 Removal of the fricative sounds that occur in the electronic stethoscope 1140311 2014 3 7 ,.,.,.,.,.,.,.,,.,.,.,.,,. i Abstract Removal of the fricative sounds that occur in the electronic stethoscope
AccessflÌfl—−ÇŠš1
 ACCESS ACCESS i ii ACCESS iii iv ACCESS v vi ACCESS CONTENTS ACCESS CONTENTS ACCESS 1 ACCESS 1 2 ACCESS 3 1 4 ACCESS 5 1 6 ACCESS 7 1 8 9 ACCESS 10 1 ACCESS 11 1 12 ACCESS 13 1 14 ACCESS 15 1 v 16 ACCESS
ACCESS ACCESS i ii ACCESS iii iv ACCESS v vi ACCESS CONTENTS ACCESS CONTENTS ACCESS 1 ACCESS 1 2 ACCESS 3 1 4 ACCESS 5 1 6 ACCESS 7 1 8 9 ACCESS 10 1 ACCESS 11 1 12 ACCESS 13 1 14 ACCESS 15 1 v 16 ACCESS
,.,.,,.,. X Y..,,., [1].,,,.,,.. HCI,,,,,,, i
![,.,.,,.,. X Y..,,., [1].,,,.,,.. HCI,,,,,,, i ,.,.,,.,. X Y..,,., [1].,,,.,,.. HCI,,,,,,, i](/thumbs/51/27619178.jpg) 23 Experimental investigation of Natural Use Profiles of Pen Pressure, Tilt and Azimuth 1120230 2012 3 1 ,.,.,,.,. X Y..,,., [1].,,,.,,.. HCI,,,,,,, i Abstract Experimental investigation of Natural Use
23 Experimental investigation of Natural Use Profiles of Pen Pressure, Tilt and Azimuth 1120230 2012 3 1 ,.,.,,.,. X Y..,,., [1].,,,.,,.. HCI,,,,,,, i Abstract Experimental investigation of Natural Use
i
 14 i ii iii iv v vi 14 13 86 13 12 28 14 16 14 15 31 (1) 13 12 28 20 (2) (3) 2 (4) (5) 14 14 50 48 3 11 11 22 14 15 10 14 20 21 20 (1) 14 (2) 14 4 (3) (4) (5) 12 12 (6) 14 15 5 6 7 8 9 10 7
14 i ii iii iv v vi 14 13 86 13 12 28 14 16 14 15 31 (1) 13 12 28 20 (2) (3) 2 (4) (5) 14 14 50 48 3 11 11 22 14 15 10 14 20 21 20 (1) 14 (2) 14 4 (3) (4) (5) 12 12 (6) 14 15 5 6 7 8 9 10 7
Microsoft Word - KUINS-Air_W10_ docx
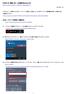 KUINS-Air 無線 LAN への接続 (Windows10) How to connect to Wi-Fi KUINS-Air (Windows10) 2019 年 7 月 KUINS-Air への接続には A ID パスワードを使用した接続 もしくは B クライアント証明書を使用した接続方法の 2 種類があります There are 2 ways to connect to KUINS-Air,
KUINS-Air 無線 LAN への接続 (Windows10) How to connect to Wi-Fi KUINS-Air (Windows10) 2019 年 7 月 KUINS-Air への接続には A ID パスワードを使用した接続 もしくは B クライアント証明書を使用した接続方法の 2 種類があります There are 2 ways to connect to KUINS-Air,
エクセルカバー入稿用.indd
 i 1 1 2 3 5 5 6 7 7 8 9 9 10 11 11 11 12 2 13 13 14 15 15 16 17 17 ii CONTENTS 18 18 21 22 22 24 25 26 27 27 28 29 30 31 32 36 37 40 40 42 43 44 44 46 47 48 iii 48 50 51 52 54 55 59 61 62 64 65 66 67 68
i 1 1 2 3 5 5 6 7 7 8 9 9 10 11 11 11 12 2 13 13 14 15 15 16 17 17 ii CONTENTS 18 18 21 22 22 24 25 26 27 27 28 29 30 31 32 36 37 40 40 42 43 44 44 46 47 48 iii 48 50 51 52 54 55 59 61 62 64 65 66 67 68
2011 Future University Hakodate 2011 System Information Science Practice Group Report Project Name Visualization of Code-Breaking RSA Group Name RSA C
 2011 Future University Hakodate 2011 System Information Science Practice Group Report Project Name RSA Group Name RSA Code Elliptic Curve Cryptograrhy Group /Project No. 13-B /Project Leader 1009087 Takahiro
2011 Future University Hakodate 2011 System Information Science Practice Group Report Project Name RSA Group Name RSA Code Elliptic Curve Cryptograrhy Group /Project No. 13-B /Project Leader 1009087 Takahiro
24_ChenGuang_final.indd
 Abstract If rapid economic development is sure to bring hierarchical consumption (M. Ozawa), the solution can only be to give property to all of the people in the country. In China, economic development
Abstract If rapid economic development is sure to bring hierarchical consumption (M. Ozawa), the solution can only be to give property to all of the people in the country. In China, economic development
soturon.dvi
 12 Exploration Method of Various Routes with Genetic Algorithm 1010369 2001 2 5 ( Genetic Algorithm: GA ) GA 2 3 Dijkstra Dijkstra i Abstract Exploration Method of Various Routes with Genetic Algorithm
12 Exploration Method of Various Routes with Genetic Algorithm 1010369 2001 2 5 ( Genetic Algorithm: GA ) GA 2 3 Dijkstra Dijkstra i Abstract Exploration Method of Various Routes with Genetic Algorithm
4.1 % 7.5 %
 2018 (412837) 4.1 % 7.5 % Abstract Recently, various methods for improving computial performance have been proposed. One of these various methods is Multi-core. Multi-core can execute processes in parallel
2018 (412837) 4.1 % 7.5 % Abstract Recently, various methods for improving computial performance have been proposed. One of these various methods is Multi-core. Multi-core can execute processes in parallel
2011 Future University Hakodate 2011 System Information Science Practice Group Report Project Name Visualization of Code-Breaking Group Name Implemati
 2011 Future University Hakodate 2011 System Information Science Practice Group Report Project Name Group Name Implemation Group /Project No. 13-C /Project Leader 1009087 Takahiro Okubo /Group Leader 1009087
2011 Future University Hakodate 2011 System Information Science Practice Group Report Project Name Group Name Implemation Group /Project No. 13-C /Project Leader 1009087 Takahiro Okubo /Group Leader 1009087
P2P P2P peer peer P2P peer P2P peer P2P i
 26 P2P Proposed a system for the purpose of idle resource utilization of the computer using the P2P 1150373 2015 2 27 P2P P2P peer peer P2P peer P2P peer P2P i Abstract Proposed a system for the purpose
26 P2P Proposed a system for the purpose of idle resource utilization of the computer using the P2P 1150373 2015 2 27 P2P P2P peer peer P2P peer P2P peer P2P i Abstract Proposed a system for the purpose
2007-Kanai-paper.dvi
 19 Estimation of Sound Source Zone using The Arrival Time Interval 1080351 2008 3 7 S/N 2 2 2 i Abstract Estimation of Sound Source Zone using The Arrival Time Interval Koichiro Kanai The microphone array
19 Estimation of Sound Source Zone using The Arrival Time Interval 1080351 2008 3 7 S/N 2 2 2 i Abstract Estimation of Sound Source Zone using The Arrival Time Interval Koichiro Kanai The microphone array
(Requirements in communication) (efficiently) (Information Theory) (certainly) (Coding Theory) (safely) (Cryptography) I 1
 (Requirements in communication) (efficiently) (Information Theory) (certainly) (oding Theory) (safely) (ryptography) I 1 (Requirements in communication) (efficiently) (Information Theory) (certainly) (oding
(Requirements in communication) (efficiently) (Information Theory) (certainly) (oding Theory) (safely) (ryptography) I 1 (Requirements in communication) (efficiently) (Information Theory) (certainly) (oding
 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 () - 1 - - 2 - - 3 - - 4 - - 5 - 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 () - 1 - - 2 - - 3 - - 4 - - 5 - 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57
社会学部紀要 114号☆/22.松村
 March 2012 1 1 1 2005 : 261 1 100 2 22 15.1 41.8 10.3 100 3 2008 : 282 23 34 70 3 114 30 4 1 2 1 2 2 1 1998 1999 2004 N 3 4 7 9 3 100 1970 March 2012 15900 42 10 15000 4 K 40 2 2 2 3 5 100 DVD 6 http :
March 2012 1 1 1 2005 : 261 1 100 2 22 15.1 41.8 10.3 100 3 2008 : 282 23 34 70 3 114 30 4 1 2 1 2 2 1 1998 1999 2004 N 3 4 7 9 3 100 1970 March 2012 15900 42 10 15000 4 K 40 2 2 2 3 5 100 DVD 6 http :
 21 VOD A study of the VOD contents decentralization delivery for unicast VOD 1100314 2010 3 1 VOD VOD Video on Demand VOD, Management Server Management Server Management Server 4 VOD CDN i Abstract A
21 VOD A study of the VOD contents decentralization delivery for unicast VOD 1100314 2010 3 1 VOD VOD Video on Demand VOD, Management Server Management Server Management Server 4 VOD CDN i Abstract A
WMN Wi-Fi MBCR i
 27 WMN Proposal of routing method that improves transmission capability in WMN 1185081 2016 2 26 WMN Wi-Fi MBCR i Abstract Proposal of routing method that improves transmission capability in WMN KOBAYASHI
27 WMN Proposal of routing method that improves transmission capability in WMN 1185081 2016 2 26 WMN Wi-Fi MBCR i Abstract Proposal of routing method that improves transmission capability in WMN KOBAYASHI
, (GPS: Global Positioning Systemg),.,, (LBS: Local Based Services).. GPS,.,. RFID LAN,.,.,.,,,.,..,.,.,,, i
 25 Estimation scheme of indoor positioning using difference of times which chirp signals arrive 114348 214 3 6 , (GPS: Global Positioning Systemg),.,, (LBS: Local Based Services).. GPS,.,. RFID LAN,.,.,.,,,.,..,.,.,,,
25 Estimation scheme of indoor positioning using difference of times which chirp signals arrive 114348 214 3 6 , (GPS: Global Positioning Systemg),.,, (LBS: Local Based Services).. GPS,.,. RFID LAN,.,.,.,,,.,..,.,.,,,
23 A Comparison of Flick and Ring Document Scrolling in Touch-based Mobile Phones
 23 A Comparison of Flick and Ring Document Scrolling in Touch-based Mobile Phones 1120220 2012 3 1 iphone..,. 2 (, ) 3 (,, ),,,.,..,. HCI i Abstract A Comparison of Flick and Ring Document Scrolling in
23 A Comparison of Flick and Ring Document Scrolling in Touch-based Mobile Phones 1120220 2012 3 1 iphone..,. 2 (, ) 3 (,, ),,,.,..,. HCI i Abstract A Comparison of Flick and Ring Document Scrolling in
yasi10.dvi
 2002 50 2 259 278 c 2002 1 2 2002 2 14 2002 6 17 73 PML 1. 1997 1998 Swiss Re 2001 Canabarro et al. 1998 2001 1 : 651 0073 1 5 1 IHD 3 2 110 0015 3 3 3 260 50 2 2002, 2. 1 1 2 10 1 1. 261 1. 3. 3.1 2 1
2002 50 2 259 278 c 2002 1 2 2002 2 14 2002 6 17 73 PML 1. 1997 1998 Swiss Re 2001 Canabarro et al. 1998 2001 1 : 651 0073 1 5 1 IHD 3 2 110 0015 3 3 3 260 50 2 2002, 2. 1 1 2 10 1 1. 261 1. 3. 3.1 2 1
企業内システムにおけるA j a x 技術の利用
 Utilization of Ajax in Enterprise Intranet Systemsby Tetsuo Yamashita, Takeshi Kuroe and Kazuhisa Ikeda Enterprise 2.0 refers to the recent trend of applying the web technologies widely deployed in Internet
Utilization of Ajax in Enterprise Intranet Systemsby Tetsuo Yamashita, Takeshi Kuroe and Kazuhisa Ikeda Enterprise 2.0 refers to the recent trend of applying the web technologies widely deployed in Internet
 (1) (2) (3) (4) (5) (6) (7) (8) (9) PLC PLC LAN MASTER PLC LAN MASTER PLC LAN MASTER PLC LAN MASTER PLC LAN MASTER MASTER MASTER PLC LAN PLC LAN PLC LAN MASTER PLC LAN MASTER MASTER TERMINAL MASTER TERMINAL
(1) (2) (3) (4) (5) (6) (7) (8) (9) PLC PLC LAN MASTER PLC LAN MASTER PLC LAN MASTER PLC LAN MASTER PLC LAN MASTER MASTER MASTER PLC LAN PLC LAN PLC LAN MASTER PLC LAN MASTER MASTER TERMINAL MASTER TERMINAL
2 ( ) i
 25 Study on Rating System in Multi-player Games with Imperfect Information 1165069 2014 2 28 2 ( ) i ii Abstract Study on Rating System in Multi-player Games with Imperfect Information Shigehiko MORITA
25 Study on Rating System in Multi-player Games with Imperfect Information 1165069 2014 2 28 2 ( ) i ii Abstract Study on Rating System in Multi-player Games with Imperfect Information Shigehiko MORITA
入門ガイド
 ii iii iv NEC Corporation 1998 v P A R 1 P A R 2 P A R 3 T T T vi P A R T 4 P A R T 5 P A R T 6 P A R T 7 vii 1P A R T 1 2 2 1 3 1 4 1 1 5 2 3 6 4 1 7 1 2 3 8 1 1 2 3 9 1 2 10 1 1 2 11 3 12 1 2 1 3 4 13
ii iii iv NEC Corporation 1998 v P A R 1 P A R 2 P A R 3 T T T vi P A R T 4 P A R T 5 P A R T 6 P A R T 7 vii 1P A R T 1 2 2 1 3 1 4 1 1 5 2 3 6 4 1 7 1 2 3 8 1 1 2 3 9 1 2 10 1 1 2 11 3 12 1 2 1 3 4 13
paper.dvi
 23 Study on character extraction from a picture using a gradient-based feature 1120227 2012 3 1 Google Street View Google Street View SIFT 3 SIFT 3 y -80 80-50 30 SIFT i Abstract Study on character extraction
23 Study on character extraction from a picture using a gradient-based feature 1120227 2012 3 1 Google Street View Google Street View SIFT 3 SIFT 3 y -80 80-50 30 SIFT i Abstract Study on character extraction
<4D6963726F736F667420506F776572506F696E74202D208376838C835B83938365815B835683878393312E707074205B8CDD8AB78382815B83685D>
 i i vi ii iii iv v vi vii viii ix 2 3 4 5 6 7 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60
i i vi ii iii iv v vi vii viii ix 2 3 4 5 6 7 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60
(Visual Secret Sharing Scheme) VSSS VSSS 3 i
 13 A Visual Secret Sharing Scheme for Continuous Color Images 10066 14 8 (Visual Secret Sharing Scheme) VSSS VSSS 3 i Abstract A Visual Secret Sharing Scheme for Continuous Color Images Tomoe Ogawa The
13 A Visual Secret Sharing Scheme for Continuous Color Images 10066 14 8 (Visual Secret Sharing Scheme) VSSS VSSS 3 i Abstract A Visual Secret Sharing Scheme for Continuous Color Images Tomoe Ogawa The
SC-85X2取説
 I II III IV V VI .................. VII VIII IX X 1-1 1-2 1-3 1-4 ( ) 1-5 1-6 2-1 2-2 3-1 3-2 3-3 8 3-4 3-5 3-6 3-7 ) ) - - 3-8 3-9 4-1 4-2 4-3 4-4 4-5 4-6 5-1 5-2 5-3 5-4 5-5 5-6 5-7 5-8 5-9 5-10 5-11
I II III IV V VI .................. VII VIII IX X 1-1 1-2 1-3 1-4 ( ) 1-5 1-6 2-1 2-2 3-1 3-2 3-3 8 3-4 3-5 3-6 3-7 ) ) - - 3-8 3-9 4-1 4-2 4-3 4-4 4-5 4-6 5-1 5-2 5-3 5-4 5-5 5-6 5-7 5-8 5-9 5-10 5-11
 2.1... 1 2.1.1.1... 1 (1). 1 (2)... 1 (3)... 1 2.1.1.2... 1 (1)... 1 (2)... 1 (3)... 1 2.1.1.3... 1 (1)... 1 (2)... 1 (3)... 1 2.1.1.4... 2 2.1.1.5... 2 2.2... 3 2.2.1... 3 2.2.1.1... 3... 3... 3 (1)...
2.1... 1 2.1.1.1... 1 (1). 1 (2)... 1 (3)... 1 2.1.1.2... 1 (1)... 1 (2)... 1 (3)... 1 2.1.1.3... 1 (1)... 1 (2)... 1 (3)... 1 2.1.1.4... 2 2.1.1.5... 2 2.2... 3 2.2.1... 3 2.2.1.1... 3... 3... 3 (1)...
05_fuke.indd
 1971 1982 1985 Abstract The first liberalisation of circuit use (1971) and the second liberalisation (1982) liberalised the use of telecommunications circuits for data communications to respond the development
1971 1982 1985 Abstract The first liberalisation of circuit use (1971) and the second liberalisation (1982) liberalised the use of telecommunications circuits for data communications to respond the development
, i
 23 The reserch of the users action patterns and the suitable delivery of coupons for them 1145120 2012 2 13 , i Abstract The reserch of the users action patterns and the suitable delivery of coupons for
23 The reserch of the users action patterns and the suitable delivery of coupons for them 1145120 2012 2 13 , i Abstract The reserch of the users action patterns and the suitable delivery of coupons for
26 Development of Learning Support System for Fixation of Basketball Shoot Form
 26 Development of Learning Support System for Fixation of Basketball Shoot Form 1175094 ,.,,.,,.,,.,,,.,,,,.,,,.,,,,, Kinect i Abstract Development of Learning Support System for Fixation of Basketball
26 Development of Learning Support System for Fixation of Basketball Shoot Form 1175094 ,.,,.,,.,,.,,,.,,,,.,,,.,,,,, Kinect i Abstract Development of Learning Support System for Fixation of Basketball
IPSJ SIG Technical Report Secret Tap Secret Tap Secret Flick 1 An Examination of Icon-based User Authentication Method Using Flick Input for
 1 2 3 3 1 Secret Tap Secret Tap Secret Flick 1 An Examination of Icon-based User Authentication Method Using Flick Input for Mobile Terminals Kaoru Wasai 1 Fumio Sugai 2 Yosihiro Kita 3 Mi RangPark 3 Naonobu
1 2 3 3 1 Secret Tap Secret Tap Secret Flick 1 An Examination of Icon-based User Authentication Method Using Flick Input for Mobile Terminals Kaoru Wasai 1 Fumio Sugai 2 Yosihiro Kita 3 Mi RangPark 3 Naonobu
一般演題(ポスター)
 6 5 13 : 00 14 : 00 A μ 13 : 00 14 : 00 A β β β 13 : 00 14 : 00 A 13 : 00 14 : 00 A 13 : 00 14 : 00 A β 13 : 00 14 : 00 A β 13 : 00 14 : 00 A 13 : 00 14 : 00 A β 13 : 00 14 : 00 A 13 : 00 14 : 00 A
6 5 13 : 00 14 : 00 A μ 13 : 00 14 : 00 A β β β 13 : 00 14 : 00 A 13 : 00 14 : 00 A 13 : 00 14 : 00 A β 13 : 00 14 : 00 A β 13 : 00 14 : 00 A 13 : 00 14 : 00 A β 13 : 00 14 : 00 A 13 : 00 14 : 00 A
IPSJ SIG Technical Report * Wi-Fi Survey of the Internet connectivity using geolocation of smartphones Yoshiaki Kitaguchi * Kenichi Nagami and Yutaka
 * Wi-Fi Survey of the Internet connectivity using geolocation of smartphones Yoshiaki Kitaguchi * Kenichi Nagami and Yutaka Kikuchi With the rapid growth in demand of smartphone use, the development of
* Wi-Fi Survey of the Internet connectivity using geolocation of smartphones Yoshiaki Kitaguchi * Kenichi Nagami and Yutaka Kikuchi With the rapid growth in demand of smartphone use, the development of
[2] 1. 2. 2 2. 1, [3] 2. 2 [4] 2. 3 BABOK BABOK(Business Analysis Body of Knowledge) BABOK IIBA(International Institute of Business Analysis) BABOK 7
![[2] 1. 2. 2 2. 1, [3] 2. 2 [4] 2. 3 BABOK BABOK(Business Analysis Body of Knowledge) BABOK IIBA(International Institute of Business Analysis) BABOK 7 [2] 1. 2. 2 2. 1, [3] 2. 2 [4] 2. 3 BABOK BABOK(Business Analysis Body of Knowledge) BABOK IIBA(International Institute of Business Analysis) BABOK 7](/thumbs/40/22240274.jpg) 32 (2015 ) [2] Projects of the short term increase at present. In order to let projects complete without rework and delays, it is important that request for proposals (RFP) are written by reflecting precisely
32 (2015 ) [2] Projects of the short term increase at present. In order to let projects complete without rework and delays, it is important that request for proposals (RFP) are written by reflecting precisely
6 2. AUTOSAR 2.1 AUTOSAR AUTOSAR ECU OSEK/VDX 3) OSEK/VDX OS AUTOSAR AUTOSAR ECU AUTOSAR 1 AUTOSAR BSW (Basic Software) (Runtime Environment) Applicat
 AUTOSAR 1 1, 2 2 2 AUTOSAR AUTOSAR 3 2 2 41% 29% An Extension of AUTOSAR Communication Layers for Multicore Systems Toshiyuki Ichiba, 1 Hiroaki Takada, 1, 2 Shinya Honda 2 and Ryo Kurachi 2 AUTOSAR, a
AUTOSAR 1 1, 2 2 2 AUTOSAR AUTOSAR 3 2 2 41% 29% An Extension of AUTOSAR Communication Layers for Multicore Systems Toshiyuki Ichiba, 1 Hiroaki Takada, 1, 2 Shinya Honda 2 and Ryo Kurachi 2 AUTOSAR, a
1., 1 COOKPAD 2, Web.,,,,,,.,, [1]., 5.,, [2].,,.,.,, 5, [3].,,,.,, [4], 33,.,,.,,.. 2.,, 3.., 4., 5., ,. 1.,,., 2.,. 1,,
![1., 1 COOKPAD 2, Web.,,,,,,.,, [1]., 5.,, [2].,,.,.,, 5, [3].,,,.,, [4], 33,.,,.,,.. 2.,, 3.., 4., 5., ,. 1.,,., 2.,. 1,, 1., 1 COOKPAD 2, Web.,,,,,,.,, [1]., 5.,, [2].,,.,.,, 5, [3].,,,.,, [4], 33,.,,.,,.. 2.,, 3.., 4., 5., ,. 1.,,., 2.,. 1,,](/thumbs/50/25936361.jpg) THE INSTITUTE OF ELECTRONICS, INFORMATION AND COMMUNICATION ENGINEERS TECHNICAL REPORT OF IEICE.,, 464 8601 470 0393 101 464 8601 E-mail: matsunagah@murase.m.is.nagoya-u.ac.jp, {ide,murase,hirayama}@is.nagoya-u.ac.jp,
THE INSTITUTE OF ELECTRONICS, INFORMATION AND COMMUNICATION ENGINEERS TECHNICAL REPORT OF IEICE.,, 464 8601 470 0393 101 464 8601 E-mail: matsunagah@murase.m.is.nagoya-u.ac.jp, {ide,murase,hirayama}@is.nagoya-u.ac.jp,
2 1 ( ) 2 ( ) i
 21 Perceptual relation bettween shadow, reflectance and luminance under aambiguous illuminations. 1100302 2010 3 1 2 1 ( ) 2 ( ) i Abstract Perceptual relation bettween shadow, reflectance and luminance
21 Perceptual relation bettween shadow, reflectance and luminance under aambiguous illuminations. 1100302 2010 3 1 2 1 ( ) 2 ( ) i Abstract Perceptual relation bettween shadow, reflectance and luminance
kut-paper-template.dvi
 26 Discrimination of abnormal breath sound by using the features of breath sound 1150313 ,,,,,,,,,,,,, i Abstract Discrimination of abnormal breath sound by using the features of breath sound SATO Ryo
26 Discrimination of abnormal breath sound by using the features of breath sound 1150313 ,,,,,,,,,,,,, i Abstract Discrimination of abnormal breath sound by using the features of breath sound SATO Ryo
kut-paper-template.dvi
 14 Application of Automatic Text Summarization for Question Answering System 1030260 2003 2 12 Prassie Posum Prassie Prassie i Abstract Application of Automatic Text Summarization for Question Answering
14 Application of Automatic Text Summarization for Question Answering System 1030260 2003 2 12 Prassie Posum Prassie Prassie i Abstract Application of Automatic Text Summarization for Question Answering








