CentreCOM AR570S 取扱説明書
|
|
|
- くにひと はしかわ
- 6 years ago
- Views:
Transcription
1 Rev.A AR570S
2
3
4 100~240V
5
6
7 Manager > HELP AR570S - V2.7 Rev /11/01 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" (# ) Help Operation SNMP Help INterface ETH BRI PRI Help ISdn ISDN Help Tdm Help FRamerelay Help PPp PPP Help VLan VLAN Help Bridge Help IP IP RIP OSPF IP Help IPV6 IPv6 Help FIrewall --More-- (<space> = next page, <CR> = one line, C = continuous, Q = quit)
8 ADD IP FILT=1 SO= SM= DES= DM= DP=23 PROT=TCP SESS=ANY AC=INCL
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27 INFO: Self tests beginning. INFO: RAM test beginning. PASS: RAM test, k bytes found. INFO: BBR tests beginning. PASS: BBR test, 512k bytes found. INFO: Self tests complete. INFO: Downloading router software. Force EPROM download (Y)? INFO: Initial download successful. INFO: Initialising Flash File System. INFO: IGMP packet trapping is active for IGMP snooping, L3FILT is activated INFO: Router startup complete login:
28 New password: rivadd Confirm: rivadd Manager > login: manager Password: friend Manager > Error ( ): SET PASSWORD, confirm password incorrect. Manager > Manager > SET PASSWORD Old password: friend
29 Manager > SET SYSTEM NAME="OSAKA" Info ( ): Operation successful. Manager OSAKA> Manager > SET TIME=13:53:00 DATE=26-MAR-2005 System time is 13:53:00 on Saturday 26-Mar OSAKA login: Manager > SHOW TIME System time is 13:54:18 on Saturday 26-Mar-2005.
30 # # SYSTEM configuration # # # SERVICE configuration # # # LOAD configuration # # # USER configuration # set user=manager pass=3af00c6... set user=manager desc="man Manager > SHOW FILE Filename Device Size Created Locks b03.rez flash MAR :37:22 0 example_isp.cfg flash MAR :29:23 0 feature.lic flash MAR :55:15 0 help.hlp flash MAR :45:09 0 longname.lfn flash MAR :38:58 0 prefer.ins flash MAR :41:16 0 random.rnd flash MAR :09:54 0 release.lic flash MAR :37:22 0 test01.cfg flash MAR :29:23 0 ud.cfg flash MAR :57: Manager > set password Old password: New password: Confirm: Manager > Manager > CREATE CONFIG=test01.cfg Manager > SHOW FILE=test01.cfg File : test01.cfg 1: 2:# 3:# SYSTEM configuration 4:# 5: 6:# 7:# LOAD configuration 8:# 9: 10:# 11:# USER configuration 12:# 13:set user=manager pass=3af0066cad11f7a6cb5db4467bce503eff priv=manager lo=yes 14:set user=manager telnet=yes desc="manager Account" 15: 16:# 17:# TTY configuration 18:# --More-- (<space> = next page, <CR> = one line, C = continuous, Q = quit)
31 Manager > SET CONFIG=test01.cfg Manager > SHOW CONFIG Boot configuration file: flash:test01.cfg (exists) Current configuration: flash:boot.cfg (default) Manager > RESTART ROUTER
32 INFO: Initialising Flash File System. INFO: IGMP packet trapping is active for IGMP snooping, L3FILT is activated INFO: Executing configuration script <flash:test01.cfg> INFO: Router startup complete login: Manager > RESTART REBOOT INFO: Self tests beginning. INFO: RAM test beginning. PASS: RAM test, k bytes found. INFO: BBR tests beginning. PASS: BBR test, 512k bytes found. INFO: Self tests complete. INFO: Downloading router software. Force EPROM download (Y)? INFO: Initial download successful. INFO: Initialising Flash File System. INFO: IGMP packet trapping is active for IGMP snooping, L3FILT is activated INFO: Executing configuration script <flash:test01.cfg> INFO: Router startup complete login: Manager > LOGOFF
33 login: manager Password: Manager > SET CONFIG=NONE login: manager Password: Info. This device is locked out temporarily (login-lockout). Manager > RESTART ROUTER login: login: manager Password: friend Manager > SHOW USER User Authentication Database Username: manager (Manager Account) Status: enabled Privilege: manager Telnet: yes Login: yes Logins: 2 Fails: 5 Sent: 0 Rcvd: 0 Authentications: 0 Fails: Active (logged in) Users User Port/Device Login Time Location manager Telnet 0 14:12:36 26-Mar Manager > DELETE FILE=*.cfg
34 Manager OSAKA> SHOW SYSTEM Router System Status Time 01:36:14 Date 05-Apr Board ID Bay Board Name Host Id Rev Serial number Base 257 AR570S 0 M2-0 D A PIC 75 0 AT-AR PIC E1/T1 PRI 0 M Memory - DRAM : kb FLASH : kb Chip Revisions SysDescription CentreCOM AR570S version B Mar-2006 SysContact SysLocation SysName OSAKA SysDistName SysUpTime ( 00:11:25 ) Boot Image : fbr size Mar-2006 Software Version: B Mar-2006 Release Version : B Oct-2005 Release built : Mar at 15:15:27 Patch Installed : NONE Territory : japan Country : none Help File : help.hlp Temperature : 38 Celsius Main Fan Speed : 5232 RPM Voltage Status ( Rail : Read ) 1.2V : 1.17V 2.5V : 2.55V 3.3V : 3.23V 5.0V : 4.89V 12.0V : 11.56V Battery voltage : 3.23V Manager OSAKA> SHOW CONFIG DYNAMIC # # SYSTEM configuration # set system name="osaka" # # SERVICE configuration # # # LOAD configuration # # # USER configuration # set user=manager pass=3af5001f767b664cad1ceb3eff0c6ab5d4 priv=manager lo=yes set user=manager desc="manager Account" telnet=yes # --More-- (<space> = next page, <CR> = one line, C = continuous, Q = quit) Manager OSAKA> SHOW CONFIG DYNAMIC=SYSTEM # # SYSTEM configuration # set system name="osaka" # # SERVICE configuration # Configuration Boot configuration file: flash:test01.cfg (exists) Current configuration: flash:test01.cfg Security Mode : Disabled Warning ( ): No patches found. Manager OSAKA>
35 Manager > set system name="osaka" Manager > SET SYSTEM NAME= OSAKA Info ( ): Operation successful. Manager > SEG SYSTEM NAME= OSAKA Error (335256): Unknown command "seg".
36 Manager >? Options : ACTivate ADD Connect CLear CREate DEACTivate DELete DESTroy DISable Disconnect DUMP EDit ENAble FINGer FLUsh Help LOAd MAIL MODify PING PURge REName Reconnect RESET RESTART SET SHow SSH STARt STop TELnet TRAce UPLoad LOGIN LOGON LOgoff LOgout Manager > Manager > SHOW? Options : ACC ALIas APPletalk BGP BOOTp BRIDge BRI BUFfer CLNS CONfig CPU DECnet DEBug DHCP DTe DTESt1 DVMrp ENCo ETH EXception FIle FEAture FIREwall FFIle FLash FRamerelay GRE GUI HTTP INSTall INTerface IP IPV6 IPSec IPX ISAkmp ISDN L2TP LAPB LAPD LDAP LOAder LOG LPD MAnager MAIL MIOX NTP NVS OSPF PATch PERM PIM PING PKT ASYn POrt PKI PPP PRI Q931 RADius RELease RSVP SA SCript SERvice SNmp SSH STAR STARTup STReam STT SWItch SYN SYStem TELnet TPAD TRAce TRIGger SESsions TCP TEST TIme TTy TACacs USEr VLAN VRRP X25C X25T TDM Manager > SHOW Manager > SHOW PPP? Options : COUnter CONFig MULTIlink IDLEtimer NAMEServers DEBUG TXSTatus TEMPlate LIMits PPPOE Manager > SHOW PPP
37 Manager > CREATE PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON PASSWORD="jK5H&2p" LQR=OFF ECHO=ON IDLE=ON Manager > CREATE PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON Manager > SET PPP=0 PASSWORD="passwd_a" Manager > SET PPP=0 OVER=eth0-any LQR=OFF ECHO=ON IDLE=ON ADD IP FILTER=1 SOURCE= SMASK= DESTINATION= DMASK= DPORT=TELNET PROTOCOL=TCP SESSION=ANY ACTION=INCLUDE Manager > ADD IP FILT=1 SO= SM= DES= DM= DP=23 PROT=TCP SESS=ANY AC=INCL ADD IP FILTER=1 SOURCE= SMASK= DESTINATION= DMASK= ACTION=INCLUDE ENTRY=1 DPORT=TELNET PROTOCOL=TCP SESSION=ANY Manager > ADD IP FILTER=1 SOURCE= SMASK= DESTINATION= DMASK= ACTION=INCLUDE Manager > SHOW IP FILTER IP Filters No. Ent. Source Port Source Address Source Mask Session Size Dest. Port Dest. Address Dest. Mask Prot.(T/C) Options Type Act/Pol/Pri Logging Matches Any Any Any General Include Off 0 Requests: 0 Passes: 0 Fails: Manager > SET IP FILTER=1 ENTRY=1 DPORT=TELNET PROTOCOL=TCP SESSION=ANY
38
39 Manager > HELP AR570S - V2.7 Rev /11/01 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" (# ) Help Operation SNMP Help INterface ETH BRI PRI Help ISdn ISDN Help Tdm Help FRamerelay Help PPp PPP Help VLan VLAN Help Bridge Help IP IP RIP OSPF IP Help IPV6 IPv6 Help FIrewall --More-- (<space> = next page, <CR> = one line, C = continuous, Q = quit)
40 Manager > H O AR570S - V2.7 Rev /11/01 Help Operation SYstem Help Operation Filesystem Help Operation Configuration Help Operation SHell Help Operation User Help Operation Authserver Help Operation LOAder Help Operation Release Help Operation Mail Help Operation SEcurity Help Operation LOG Help Operation SCript Help Operation TRigger Help Operation SNmp SNMP Help Operation Ntp NTP --More-- (<space> = next page, <CR> = one line, C = continuous, Q = quit) IP ADD IP INTERFACE IPV6 ADD IPV6 INTERFACE ETH VLAN PPP FR BRIDGE ADD BRIDGE PORT Manager > H O SY CREATE VLAN ADD VLAN PORT CREATE PPP CREATE FRAMERELAY AR570S - V2.7 Rev /11/01 ETH PORT ISDN TDM L2TP / ADD ISDN CALL CREATE TDM GROUP ADD L2TP CALL DISABLE HTTP SERVER EDIT [filename] ENABLE HTTP SERVER HELP [topic] LOGIN [login-name] LOGOFF RESTART {REBOOT ROUTER} [CONFIG={filename NONE}] SET HELP=filename SET SYSTEM CONTACT=string SET SYSTEM DISTINGUISHEDNAME={dist-name NONE} SET SYSTEM LOCATION=string SET SYSTEM NAME=string SET SYSTEM TERRITORY={AUSTRALIA CHINA EUROPE JAPAN KOREA NEWZEALAND USA} SET [TIME=time] [DATE=date] --More-- (<space> = next page, <CR> = one line, C = continuous, Q = quit) ETH PORT BRI PRI IP
41
42 Manager > ADD IP INTERFACE=vlan1 IP= MASK= Manager > ADD IP INTERFACE=vlan-default IP= MASK=
43 Manager > CREATE PPP=0 OVER=eth0-any Manager > CREATE PPP=0 OVER=TDM-remote Manager > CREATE FR=0 OVER=TDM-remote LMIS- CHEME=ANNEXD Manager > RESET FR=0 Manager > CREATE PPP=0 OVER=ISDN-remote IDLE=ON
44 Manager > ENABLE IP Manager > ADD IP INT=VLAN1 IP= MASK= Manager > ENABLE IP Info ( ): IP module has been enabled. Manager > ADD IP INT=VLAN1 IP= Info ( ): interface successfully added. Manager > SHOW CONFIG DYN=IP # # IP configuration # enable ip add ip int=vlan1 ip= Manager > ADD IP INT=ETH0 IP= MASK= Manager > SHOW IP INTERFACE Interface Type IP Address Bc Fr PArp Filt RIP Met. SAMode IPSc Pri. Filt Pol.Filt Network Mask MTU VJC GRE OSPF Met. DBcast Mul Local --- Not set Pass Not set vlan1 Static n Off Pass No No Rec eth0 Static n On Pass No No Rec Manager > ADD IP INT=VLAN1-1 IP= Info ( ): interface successfully added. Manager > SHOW CONFIG DYN=IP # # IP configuration # enable ip add ip int=vlan1-0 ip= add ip int=vlan1-1 ip= Manager > ADD IP INT=PPP0 IP= MASK=
45 Manager X-Y> ADD IP INTERFACE=eth0 IP= MASK= Info ( ): interface successfully added. Manager > SHOW IP INTERFACE Interface Type IP Address Bc Fr PArp Filt RIP Met. SAMode IPSc Pri. Filt Pol.Filt Network Mask MTU VJC GRE OSPF Met. DBcast Mul Local --- Not set Pass Not set vlan1 Static n Off Pass No No Rec eth0 Static n On Pass No No Rec Manager X-Y> SHOW IP ROUTE login:manager Password:friend IP Routes Destination Mask NextHop Interface Age DLCI/Circ. Type Policy Protocol Metrics Preference vlan direct 0 interface eth0 7 - direct 0 interface Manager > SET SYSTEM NAME=X-Y Info (134003): Operation successful. Manager X-Y> Manager X-Y> ENABLE IP Info ( ): IP module has been enabled. Manager X-Y> ADD IP INTERFACE=vlan1 IP= MASK= Info ( ): interface successfully added.
46 Manager Y-Z> ENABLE IP Info ( ): IP module has been enabled. Manager Y-Z> ADD IP INTERFACE=vlan1 IP= MASK= Info ( ): interface successfully added. Manager Y-Z> ADD IP INTERFACE=eth0 IP= MASK= Info ( ): interface successfully added. login:manager Password:friend Manager > SET SYSTEM NAME=Y-Z Info (134003): Operation successful. Manager Y-Z> Manager Y-Z> SHOW IP ROUTE IP Routes Destination Mask NextHop Interface Age DLCI/Circ. Type Policy Protocol Metrics Preference vlan direct 0 interface eth0 6 - direct 0 interface
47 Manager X-Y> ADD IP ROUTE= MASK= INTERFACE=eth0 NEXTHOP= METRIC=2 Info ( ): IP route successfully added. Manager X-Y> SHOW IP ROUTE IP Routes Destination Mask NextHop Interface Age DLCI/Circ. Type Policy Protocol Metrics Preference vlan direct 0 interface eth direct 0 interface eth0 5 - remote 0 static Manager Y-Z> ADD IP ROUTE= MASK= INTERFACE=vlan1 NEXTHOP= METRIC=2 Info ( ): IP route successfully added. Manager Y-Z> SHOW IP ROUTE IP Routes Destination Mask NextHop Interface Age DLCI/Circ. Type Policy Protocol Metrics Preference vlan1 9 - remote 0 static vlan direct 0 interface eth direct 0 interface
48 Manager X-Y> ADD IP ROUTE= MASK= INTERFACE=vlan1 NEXTHOP= METRIC=2 Info ( ): IP route successfully added. Manager Y-Z> ADD IP ROUTE= MASK= INTERFACE=vlan1 NEXTHOP= METRIC=2 Info ( ): IP route successfully added. Manager X-Y> SHOW IP ROUTE IP Routes Destination Mask NextHop Interface Age DLCI/Circ. Type Policy Protocol Metrics Preference vlan1 6 - remote 0 static vlan direct 0 interface eth direct 0 interface eth remote 0 static Manager GW> ADD IP ROUTE= MASK= INTERFACE=vlan1 NEXTHOP= METRIC=2 Manager GW> ADD IP ROUTE= MASK= INTERFACE=vlan1 NEXTHOP= METRIC=2 Manager Y-Z> ADD IP ROUTE= MASK= INTERFACE=vlan1 NEXTHOP= METRIC=2 Info ( ): IP route successfully added. Manager Y-Z> SHOW IP ROUTE IP Routes Destination Mask NextHop Interface Age DLCI/Circ. Type Policy Protocol Metrics Preference vlan1 3 - remote 0 static vlan remote 0 static vlan direct 0 interface eth direct 0 interface
49
50 login: manager Password: Manager > ADD USER=osaka-shisya PASSWORD= okonomiyaki LOGIN=NO Manager > ADD USER=osaka-shisya PASSWORD= okonomiyaki LOGIN=NO This is a security command, enter your password at the prompt Password: Manager > SET USER SECUREDELAY=90 This is a security command, enter your password at the prompt Password: User module configuration and counters Security parameters login failures before lockout... 5 (LOGINFAIL) lockout period seconds (LOCKOUTPD) manager password failures before logoff.. 3 (MANPWDFAIL) maximum security command interval seconds (SECURDELAY) minimum password length... 6 characters (MINPWDLEN) TACACS retries... 3 (TACRETRIES) TACACS timeout period... 5 seconds (TACTIMEOUT) semi-permanent manager port... none Security counters logins 2 authentications 0 managerpwdchanges 0 defaultacctrecoveries 1 unknownloginnames 0 tacacsloginreqs 0 totalpwdfails 0 tacacsloginrejs 0 managerpwdfails 0 tacacsreqtimeouts 0 securitycmdlogoffs 0 tacacsreqfails 0 loginlockouts 0 databasecleartotallys Manager > SET USER=osaka-shisya LOGIN=yes DESC= osaka-shisya PPP account This is a security command, enter your password at the prompt Password: User Authentication Database Username: osaka-shisya (osaka-shisya PPP account) Status: enabled Privilege: user Telnet: no Login: yes Logins: 0 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails: User Authentication Database Username: osaka-shisya () Status: enabled Privilege: user Telnet: no Login: no Logins: 0 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails:
51 login: osaka-shisya Password: > SET PASSWORD OLD passsowd: New password: Confirm: Manager > SHOW USER User Authentication Database Username: manager (Manager Account) Status: enabled Privilege: manager Telnet: yes Login: yes Logins: 4 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails: 0 Username: osaka-shisya (osaka-shisya PPP account) Status: enabled Privilege: user Telnet: no Login: yes Logins: 0 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails: Manager > DELETE USER=osaka-shisya This is a security command, enter your password at the prompt Password: Info (145265): DELETE USER, user osaka-shisya has been deleted. Manager > PURGE USER This is a security command, enter your password at the prompt Password: Info (145269): PURGE USER, user database has been purged. Manager > SHOW USER Username: manager (Manager Account) Status: enabled Privilege: manager Telnet: yes Login: yes Logins: 0 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails: Active (logged in) Users User Port/Device Login Time Location manager Asyn 0 15:52:20 26-Mar-2005 local
52 Manager > ADD USER=secoff PRIVILEGE=SECURITYOFFICER PASSWORD="top secret" Manager > ENABLE USER RSO This is a security command, enter your password at the prompt Password: Info ( ): RSO has been enabled. Manager > ADD USER RSO IP= Remote Security Officer Access is enabled Remote Security Officer / Manager > CREATE CONFIG=TEST01.CFG Info ( ): Operation successful. Manager > SET CONFIG=TEST01.CFG Info ( ): Operation successful. Manager > ENABLE SYSTEM SECURITY_MODE Info ( ): Operation successful. Manager > LOGIN secoff Password: SecOff > SecOff > add user=nagoya-sisya password="misokatsu" login=no This is a security command, enter your password at the prompt Password: Number of logged in Security Officers currently active...1 User Authentication Database Username: nagoya-sisya () Status: enabled Privilege: user Telnet: no Login: no Logins: 0 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails:
53 SecOff > SET USER SECUREDELAY=90 This is a security command, enter your password at the prompt Password: User module configuration and counters Security parameters login failures before lockout... 5 (LOGINFAIL) lockout period seconds (LOCKOUTPD) manager password failures before logoff.. 3 (MANPWDFAIL) maximum security command interval seconds (SECURDELAY) minimum password length... 6 characters (MINPWDLEN) TACACS retries... 3 (TACRETRIES) TACACS timeout period... 5 seconds (TACTIMEOUT) semi-permanent manager port... none Security counters logins 5 authentications 0 managerpwdchanges 0 defaultacctrecoveries 2 unknownloginnames 0 tacacsloginreqs 0 totalpwdfails 2 tacacsloginrejs 0 managerpwdfails 0 tacacsreqtimeouts 0 securitycmdlogoffs 0 tacacsreqfails 0 loginlockouts 0 databasecleartotallys Manager > DISABLE SYSTEM SECURITY_MODE Warning: This command will disable security mode and delete all security files. Are you sure you wish to proceed?(y/n) y Info ( ): Operation successful.
54
55 Manager > EDIT ROUTER.CFG # # SYSTEM configuration # # # SERVICE configuration # # # LOAD configuration # # # USER configuration # set user=manager pass=3af116ce503efb5dbf7a00c6cad64467bf priv=manager lo=yes set user=manager desc="manager Account" telnet=yes # # TTY configuration # Ctrl+K+H = Help File = ROUTER.CFG Insert 1:1 Lose changes ( y/n )? Y Save file ( y/n )? Y
56
57 Manager > ENABLE IP Manager > ADD IP INT=vlan1 IP= TELNET ENABLE BRIDGE ADD BRIDGE PROTOCOL="ALL ETHERNET II" TYPE=ALLETHII PRIO=1 ADD BRIDGE PROTOCOL="IP" TYPE=IP PRIO=1 ADD BRIDGE PROTOCOL="ARP" TYPE=ARP PRIO=1 ADD BRID PO=1 INT=vlan1 ADD BRID PO=2 INT=eth0 ENABLE IP ADD IP INT=eth0 IP= TELNET TELNET session now in ESTABLISHED state login: TELNET session now in ESTABLISHED state login: manager Password: friend Manager >
58 Manager > TELNET Manager > ADD IP HOST=pearl IP= Manager > TELNET pearl Manager > ADD IP PRIMARY= Manager > TELNET spankfire.deilla.co.jp
59 Manager > ping Echo reply 1 from time delay 1 ms Echo reply 2 from time delay 1 ms Echo reply 3 from time delay 1 ms Echo reply 4 from time delay 1 ms Echo reply 5 from time delay 1 ms Manager > trace Trace from to , 1-30 hops (ms) (ms) ? 40? (ms) *** Target reached Manager > ping sipa=
60
61 show file show file=filename.cfg upload file=filename.cfg server=ip-addr upload file=filename.cfg method=zmodem port=0 load file=filename.cfg server=ip-addr destination=flash load method=zmodem port=0 destination=flash show config dynamic create config=filename.cfg edit filename.cfg set config=filename.cfg restart router restart reboot Manager > SHOW FILE Filename Device Size Created Locks b03.rez flash MAR :37:22 0 example_isp.cfg flash MAR :29:23 0 feature.lic flash MAR :55:15 0 help.hlp flash MAR :45:09 0 longname.lfn flash MAR :38:58 0 prefer.ins flash MAR :41:16 0 random.rnd flash MAR :09:54 0 release.lic flash MAR :37:22 0 test01.cfg flash MAR :29:23 0 ud.cfg flash MAR :57:
62 Manager > SHOW FLASH FFS info: global operation... none flash autowrite... disabled compaction count est compaction time seconds files bytes (28 files) garbage bytes free bytes required free block bytes total bytes diagnostic counters: event successes failures get 0 0 open 0 0 read 15 0 close 8 0 complete 0 0 write 0 0 create 0 0 put 0 0 delete 0 0 check 1 0 erase 0 0 compact 0 0 verify [device:]filename.ext Manager > ACTIVATE FLASH COMPACTION Info (131260): Flash compacting... DO NOT restart the router until compaction is completed. Manager > Info (131261): Flash compaction successfully completed.
63
64 Manager > SHOW FILE=*.cfg Filename Device Size Created Locks catv.cfg flash May :48: perso.cfg flash May :00: mulho.cfg flash May :36:19 0 example_isp.cfg flash Mar :29:23 0 telnet.cfg flash Apr :11:25 0 tokyo.cfg flash May :30:02 0 tokyo.scp flash May :45:06 0 x-y.cfg flash May :44:19 0 y-z.cfg flash May :46: Manager > SHOW FILE=t*.* Filename Device Size Created Locks telnet.cfg flash Apr :11:25 0 tokyo.cfg flash May :30:02 0 tokyo.scp flash May :45: Manager > DELETE FILE=no*.scp Manager > DELETE FILE=*:no*.scp
65 Manager> LOAD FILE=test01.cfg SERVER= DESTINATION=FLASH Manager > Info ( ): File transfer successfully completed. Manager > ENABLE IP Manager > ADD IP INT=vlan1 IP= Manager> UPLOAD FILE=test01.cfg SERVER= Manager > Info ( ): File transfer successfully completed.
66 Manager> UPLOAD FILE=TOOS.cfg METHOD=ZMODEM ASYN=0 Manager> LOAD METHOD=ZMODEM ASYN=0 DESTINATION=FLASH
67
68
69 login: manager Password: Manager > SHOW LOG Date/Time S Mod Type SType Message :18:02 4 ENCO ENCO PAC M18X Security Engine Found :18:02 4 ENCO ENCO PAC M18X Security Engine Initialised :18:02 3 LOG IGMP packet trapping is active for IGMP snooping, L3FILT is activated 26 14:18:02 4 ENCO ENCO STAC STAC SW Initialised 26 14:18:02 7 SYS REST NORM Router startup, ver B-03, 04-MAR-2006, Clock Log: 14:17:13 on 26-MAR :18:02 6 PRI PINT WARN pri(0): interface reset 26 14:18:04 6 PRI PINT DOWN pri(0): Interface is no longer receiving incoming signal 26 14:18:16 3 DHCP DHCP IP address bound to f4-95-9c :18:31 3 DHCP DHCP IP address bound to e-b3-bb 26 14:18:51 3 USER USER LON manager login on port :18:55 3 CH MSG WARN No patches found 26 14:20:39 3 CH MSG WARN No patches found 26 15:18:16 3 DHCP DHCP IP address bound to --More-- (<space> = next page, <CR> = one line, C = continuous, Q = quit) INFO: Self tests beginning. INFO: RAM test beginning. PASS: RAM test, 65536k bytes found. INFO: Self tests complete. INFO: Downloading router software. Force EPROM download (Y)? INFO: Initial download successful. INFO: Initialising Flash File System. INFO: IGMP packet trapping is active for IGMP snooping, L3FILT is activated INFO: Executing configuration script <flash:boot.cfg> INFO: Router startup complete login:
70
71
72
73
74
75 Manager > ADD IP ROUTE= INT=ppp0 NEXTHOP= Info ( ): IP route successfully added.
76
77 Manager > ENABLE IP REMOTEASSIGN Info ( ): Remote IP assignment has been enabled. login: manager Password: friend Manager > CREATE PPP=0 OVER=eth0-any Info ( ): Operation successful. Manager > SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON PASSWORD=passwd_a LQR=OFF ECHO=ON Info ( ): Operation successful. Manager > ENABLE IP Manager > ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager > ADD IP INT=ppp0 IP= Info ( ): interface successfully added. Manager > ADD IP ROUTE= INT=ppp0 NEXTHOP= Info ( ): IP route successfully added. Manager > ENABLE IP DNSRELAY Info ( ): Operation successful. Manager > SET IP DNSRELAY INT=ppp0 Info ( ): Operation successful. Info ( ): IP module has been enabled.
78 Manager > ENABLE FIREWALL Info ( ): 19-Apr :55:22 Firewall enabled. Manager > CREATE FIREWALL POLICY=net Manager > ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH Manager > ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC Manager > ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 Manager > ENABLE DHCP Info ( ): Operation successful. Manager > DISABLE FIREWALL POLICY=net IDENTPROXY Manager > CREATE DHCP POLICY=BASE LEASETIME=7200 Info ( ): Operation successful. Manager > ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE Manager > ADD DHCP POLICY=BASE SUBNET= ROUTER= DNSSERVER= Info ( ): Operation successful. Manager > CREATE DHCP RANGE=LOCAL POLICY=BASE IP= NUMBER=32 Info ( ): Operation successful.
79 Manager > SET TIME=01:00:01 DATE=01-APR-2005 System time is 01:00:01 on Sunday 01-APR Manager > SET PASSWORD Old password: friend New password: xxxxxxx Confirm: xxxxxxx Manager > CREATE CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager > SET CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager > SHOW PPP Name Enabled ifindex Over CP State ppp0 YES 04 IPCP OPENED eth0-any LCP OPENED Manager > SHOW INT Interfaces sysuptime: 01:26:55 DynamicLinkTraps...Disabled TrapLimit...20 Number of unencrypted PPP/FR links...1 ifindex Interface ifadminstatus ifoperstatus iflastchange eth0 Up Up 01:17:13 3 vlan1 Up Up 00:00:01 4 ppp0 Up Up 01:17: Manager > SHOW PPP CONFIG Interface - description Parameter Configured Negotiated ppp0 - Local Peer eth0-any IP IP Compression Protocol NONE NONE VJC IP Pool NOT SET IP Address Request ON IP Address Primary DNS Address NONE Secondary DNS Address NONE Primary WinS Address NOT SET NONE Secondary WinS Address NOT SET NONE PPPoE Session ID B1CC B1CC MAC Address of Peer a-0a-04 Service Name any Debug Maximum packet bytes to display
80 1 CREATE PPP=0 OVER=eth0-any 2 SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON [email protected] PASSWORD=passwd_a LQR=OFF ECHO=ON 3 ENABLE IP 4 ENABLE IP REMOTEASSIGN 5 ADD IP INT=vlan1 IP= MASK= ADD IP INT=ppp0 IP= ADD IP ROUTE= INT=ppp0 NEXTHOP= ENABLE IP DNSRELAY 9 SET IP DNSRELAY INT=ppp0 10 ENABLE FIREWALL 11 CREATE FIREWALL POLICY=net 12 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH 13 DISABLE FIREWALL POLICY=net IDENTPROXY 14 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 15 ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC 16 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 17 ENABLE DHCP 18 CREATE DHCP POLICY=BASE LEASETIME= ADD DHCP POLICY=BASE SUBNET= ROUTER= DNSSERVER= CREATE DHCP RANGE=LOCAL POLICY=BASE IP= NUMBER=32
81 Manager > CREATE PPP=0 OVER=eth0-any Info ( ): Operation successful. Manager > SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON PASSWORD=passwd_a LQR=OFF ECHO=ON Info ( ): Operation successful. Manager > ENABLE IP Info ( ): IP module has been enabled. Manager > ENABLE IP REMOTEASSIGN Info ( ): Remote IP assignment has been enabled. login: manager Password: friend
82 Manager > ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager > ADD IP INT=ppp0 IP= Info ( ): interface successfully added. Manager > ADD IP ROUTE= INT=ppp0 NEXTHOP= Info ( ): IP route successfully added. Manager > ENABLE FIREWALL Info ( ): 19-Apr :55:22 Firewall enabled. Manager > CREATE FIREWALL POLICY=net Manager > DISABLE FIREWALL POLICY=net IDENTPROXY Manager > ADD FIREWALL POLICY=net INT=VLAN1 TYPE=PRIVATE Manager > ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC Manager > ADD FIREWALL POLICY=net RULE=1 AC=ALLOW INT=ppp0 PROTO=TCP IP= PORT=25 Manager > ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH
83 Manager > ADD FIREWALL POLICY=net RULE=2 AC=ALLOW INT=ppp0-0 PROTO=TCP IP= PORT=53 Manager > ADD FIREWALL POLICY=net RULE=2 AC=ALLOW INT=ppp0-0 PROTO=UDP IP= PORT=53 Manager > SET TIME=01:00:01 DATE=01-APR-2005 System time is 01:00:01 on Sunday 01-APR Manager > SHOW PPP Name Enabled ifindex Over CP State ppp0 YES 04 IPCP OPENED eth0-any LCP OPENED Manager > SHOW INT Interfaces sysuptime: 01:26:55 DynamicLinkTraps...Disabled TrapLimit...20 Number of unencrypted PPP/FR links...1 ifindex Interface ifadminstatus ifoperstatus iflastchange eth0 Up Up 01:17:13 3 vlan1 Up Up 00:00:01 4 ppp0 Up Up 01:17: Manager > SET PASSWORD Old password: friend New password: xxxxxxx Confirm: xxxxxxx Manager > CREATE CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager > SET CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager > SHOW PPP CONFIG Interface - description Parameter Configured Negotiated ppp0 - Local Peer eth0-any IP IP Compression Protocol NONE NONE VJC IP Pool NOT SET IP Address Request ON IP Address Primary DNS Address NONE Secondary DNS Address NONE Primary WinS Address NOT SET NONE Secondary WinS Address NOT SET NONE PPPoE Session ID B1CC B1CC MAC Address of Peer a-0a-04 Service Name any Debug Maximum packet bytes to display
84 1 CREATE PPP=0 OVER=eth0-any 2 SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON [email protected] PASSWORD=passwd_a LQR=OFF ECHO=ON 3 ENABLE IP 4 ENABLE IP REMOTEASSIGN 5 ADD IP INT=VLAN1 IP= MASK= ADD IP INT=ppp0 IP= ADD IP ROUTE= INT=ppp0 NEXTHOP= ENABLE FIREWALL 9 CREATE FIREWALL POLICY=net 10 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH 11 DISABLE FIREWALL POLICY=net IDENTPROXY 12 ADD FIREWALL POLICY=net INT=VLAN1 TYPE=PRIVATE 13 ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC 14 ADD FIREWALL POLICY=net RULE=1 AC=ALLOW INT=ppp0 PROTO=TCP IP= PORT=25 15 ADD FIREWALL POLICY=net RULE=2 AC=ALLOW INT=ppp0 PROTO=TCP IP= PORT=53 16 ADD FIREWALL POLICY=net RULE=3 AC=ALLOW INT=ppp0 PROTO=UDP IP= PORT=53
85 login: manager Password: friend Manager > CREATE PPP=0 OVER=eth0-any Info ( ): Operation successful. Manager > SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON PASSWORD=passwd_a LQR=OFF ECHO=ON Info ( ): Operation successful. Manager > ENABLE IP Info ( ): IP module has been enabled.
86 Manager > ENABLE IP REMOTEASSIGN Info ( ): Remote IP assignment has been enabled. Manager > ADD IP INT=eth1 IP= MASK= Info ( ): interface successfully added. Manager > ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager > ADD IP INT=ppp0 IP= Info ( ): interface successfully added. Manager > ADD IP ROUTE= INT=ppp0 NEXTHOP= Info ( ): IP route successfully added. Manager > ENABLE FIREWALL Info ( ): 19-Apr :55:22 Firewall enabled. Manager > CREATE FIREWALL POLICY=net Manager > ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH Manager > DISABLE FIREWALL POLICY=net IDENTPROXY Manager > ADD FIREWALL POLICY=net INT=eth1 TYPE=PRIVATE Manager > ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE
87 Manager > ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC Manager > ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 GBLIP= Manager > ADD FIREWALL POLICY=net RULE=1 AC=ALLOW INT=ppp0 PROTO=TCP IP= PORT=80 Manager > ADD FIREWALL POLICY=net RULE=3 AC=ALLOW INT=ppp0 PROTO=TCP IP= PORT=53 Manager > ADD FIREWALL POLICY=net RULE=4 AC=ALLOW INT=ppp0 PROTO=UDP IP= PORT=53 Manager > SET TIME=01:00:01 DATE=01-APR-2005 System time is 01:00:01 on Sunday 01-APR Manager > SET PASSWORD Old password: friend New password: xxxxxxx Confirm: xxxxxxx Manager > ADD FIREWALL POLICY=net RULE=2 AC=ALLOW INT=ppp0 PROTO=TCP IP= PORT=25 Manager > CREATE CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager > SET CONFIG=ROUTER.CFG Info ( ): Operation successful.
88 Manager > SHOW PPP Name Enabled ifindex Over CP State ppp0 YES 04 IPCP OPENED eth0-any LCP OPENED Manager > SHOW INT Interfaces sysuptime: 01:26:55 DynamicLinkTraps...Disabled TrapLimit...20 Number of unencrypted PPP/FR links...1 ifindex Interface ifadminstatus ifoperstatus iflastchange eth0 Up Up 01:17:13 3 vlan1 Up Up 00:00:01 4 ppp0 Up Up 01:17: Manager > SHOW PPP CONFIG Interface - description Parameter Configured Negotiated ppp0 - Local Peer eth0-any IP IP Compression Protocol NONE NONE VJC IP Pool NOT SET IP Address Request ON IP Address Primary DNS Address NONE Secondary DNS Address NONE Primary WinS Address NOT SET NONE Secondary WinS Address NOT SET NONE PPPoE Session ID B1CC B1CC MAC Address of Peer a-0a-04 Service Name any Debug Maximum packet bytes to display CREATE PPP=0 OVER=eth0-any 2 SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON [email protected] PASSWORD=passwd_a LQR=OFF ECHO=ON 3 ENABLE IP 4 ENABLE IP REMOTEASSIGN 5 ADD IP INT=eth1 IP= MASK= ADD IP INT=vlan1 IP= MASK= ADD IP INT=ppp0 IP= ADD IP ROUTE= INT=ppp0 NEXTHOP= ENABLE FIREWALL 10 CREATE FIREWALL POLICY=net 11 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH 12 DISABLE FIREWALL POLICY=net IDENTPROXY 13 ADD FIREWALL POLICY=net INT=eth1 TYPE=PRIVATE 14 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 15 ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC 16 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 GBLIP= ADD FIREWALL POLICY=net RULE=1 AC=ALLOW INT=ppp0 PROTO=TCP IP= PORT=80 18 ADD FIREWALL POLICY=net RULE=2 AC=ALLOW INT=ppp0 PROTO=TCP IP= PORT=25 19 ADD FIREWALL POLICY=net RULE=3 AC=ALLOW INT=ppp0 PROTO=TCP IP= PORT=53 20 ADD FIREWALL POLICY=net RULE=4 AC=ALLOW INT=ppp0 PROTO=UDP IP= PORT=53
89
90 login: manager Password: friend Manager > ENABLE IP Info ( ): IP module has been enabled. Manager > ENABLE IP REMOTEASSIGN Info ( ): Remote IP assignment has been enabled. Manager > ADD IP INT=eth0 IP=DHCP Info ( ): interface successfully added. Manager > ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager > ENABLE IP DNSRELAY Info ( ): Operation successful. Manager > ENABLE FIREWALL Info ( ): 19-Apr :55:22 Firewall enabled. Manager > CREATE FIREWALL POLICY=net Manager > ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH Manager > DISABLE FIREWALL POLICY=net IDENTPROXY
91 Manager > ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE Manager > ADD FIREWALL POLICY=net INT=eth0 TYPE=PUBLIC Manager > ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=eth0 Manager > ENABLE DHCP Info ( ): Operation successful. Manager > CREATE DHCP POLICY=BASE LEASETIME=7200 Info ( ): Operation successful. Manager > ADD DHCP POLICY=BASE SUBNET= ROUTER= DNSSERVER= Info ( ): Operation successful. Manager > CREATE DHCP RANGE=LOCAL POLICY=BASE IP= NUMBER=32 Info ( ): Operation successful. Manager > SET SYSTEM NAME=zy a Manager zy a> SET TIME=01:00:01 DATE=01-APR-2005 System time is 01:00:01 on Sunday 01-APR Manager zy a> SET PASSWORD Old password: friend New password: xxxxxxx Confirm: xxxxxxx
92 Manager zy a> CREATE CONF=ROUTER.CFG Info ( ): Operation successful. Manager zy a> SET CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager zy a> SHOW DHCP DHCP Server State... enabled BOOTP Status... disabled Debug Status... disabled Policies... BASE Ranges... LOCAL ( ) In Messages... 6 Out Messages In DHCP Messages... 6 Out DHCP Messages In BOOTP Messages... 0 Out BOOTP Messages... 0 DHCP Client Interface... eth0 State... bound Server Assigned Domain... myisp.ne.jp Assigned IP Assigned Mask Assigned Gateway Assigned DNS Assigned Lease ENABLE IP 2 ENABLE IP REMOTEASSIGN 3 ADD IP INT=eth0 IP=DHCP 4 ADD IP INT=vlan1 IP= MASK= ENABLE IP DNSRELAY 6 ENABLE FIREWALL 7 CREATE FIREWALL POLICY=net 8 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH 9 DISABLE FIREWALL POLICY=net IDENTPROXY 10 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 11 ADD FIREWALL POLICY=net INT=eth0 TYPE=PUBLIC 12 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=eth0 13 ENABLE DHCP 14 CREATE DHCP POLICY=BASE LEASETIME= ADD DHCP POLICY=BASE SUBNET= ROUTER= DNSSERVER= CREATE DHCP RANGE=LOCAL POLICY=BASE IP= NUMBER=32 17 SET SYSTEM NAME=zy a
93
94 login: manager Password: friend Manager > SET SYSTEM NAME=A Info ( ): Operation successful. Manager A> Manager A> ADD USER=secoff PASSWORD=passwdSA PRIVILEGE=SECURITYOFFICER User Authentication Database Username: secoff () Status: enabled Privilege: Sec Off Telnet: no Login: yes Logins: 0 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails:
95 Manager A> CREATE PPP=0 OVER=eth0-any Info ( ): Operation successful. Manager A> SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON PASSWORD=passwd_a LQR=OFF ECHO=ON Info ( ): Operation successful. Manager A> ENABLE IP Info ( ): IP module has been enabled. Manager A> ENABLE IP REMOTEASSIGN Info ( ): Remote IP assignment has been enabled. Manager A> ADD IP INT=eth1 IP= MASK= Manager A> ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager A> ADD IP INT=ppp0-0 IP= Info ( ): interface successfully added. Manager A> ADD IP INT=ppp0-1 IP= MASK= Info ( ): interface successfully added. Manager A> ADD IP ROUTE= INT=ppp0-1 NEXTHOP= Info ( ): IP route successfully added. Manager A> ENABLE FIREWALL Info ( ): 19-Apr :55:22 Firewall enabled. Info ( ): interface successfully added.
96 Manager A> CREATE FIREWALL POLICY=net Manager A> ADD FIREWALL POLICY=net INT=ppp0-1 TYPE=PUBLIC Manager A> ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH Manager A> ADD FIREWALL POLICY=net INT=ppp0-1 TYPE=PUBLIC Manager A> DISABLE FIREWALL POLICY=net IDENTPROXY Manager A> ADD FIREWALL POLICY=net INT=eth1 TYPE=PRIVATE Manager A> ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0-1 GBLIP= Manager A> ADD FIREWALL POLICY=net RULE=1 AC=ALLOW INT=ppp0-1 PROTO=TCP IP= PORT=80 Manager A> ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE Manager A> ADD FIREWALL POLICY=net RULE=2 AC=ALLOW INT=ppp0-1 PROTO=TCP IP= PORT=25
97 Manager A> ADD FIREWALL POLICY=net RULE=3 AC=ALLOW INT=ppp0-1 PROTO=TCP IP= PORT=53 Manager A> ADD FIREWALL POLICY=net RULE=4 AC=ALLOW INT=ppp0-1 PROTO=UDP IP= PORT=53 Manager A> ADD FIREWALL POLICY=net RU=5 AC=ALLOW INT=ppp0-1 PROTO=UDP GBLPO=500 GBLIP= PO=500 IP= Manager A> ADD FIREWALL POLICY=net RU=6 AC=NONAT INT=vlan1 PROT=ALL IP= Manager A> SET FIREWALL POLICY=net RU=6 REMOTEIP= Manager A> ADD FIREWALL POLICY=net RU=7 AC=NONAT INT=ppp0-1 PROT=ALL IP= ENCAP=IPSEC Manager A> CREATE ENCO KEY=1 TYPE=GENERAL VALUE="secret" Info ( ): Operation successful. Manager A> CREATE ISAKMP POLICY="i" PEER= KEY=1 SENDN=TRUE Info ( ): Operation successful. Manager A> CREATE IPSEC SASPEC=1 KEYMAN=ISAKMP PROTOCOL=ESP ENCALG=DES HASHALG=SHA Info ( ): Operation successful. Manager A> CREATE IPSEC BUNDLE=1 KEYMAN=ISAKMP STRING="1" Info ( ): Operation successful.
98 Manager A> CREATE IPSEC POLICY="isa" INT=ppp0-1 ACTION=PERMIT LPORT=500 RPORT=500 TRANSPORT=UDP Info ( ): Operation successful. Manager A> CREATE IPSEC POLICY="vpn" INT=ppp0-1 ACTION=IPSEC KEYMAN=ISAKMP BUNDLE=1 PEER= Info ( ): Operation successful. Manager A> SET IPSEC POLICY="vpn" LAD= LMA= RAD= RMA= Info ( ): Operation successful. Manager A> CREATE IPSEC POLICY="inet" INT=ppp0-1 ACTION=PERMIT Info ( ): Operation successful. Manager A> ENABLE IPSEC Info ( ): Operation successful. Manager A> ENABLE ISAKMP Info ( ): ISAKMP has been enabled. Manager A> LOGIN secoff Password: passwdsa SecOff A> ENABLE SYSTEM SECURITY_MODE Info ( ): Operation successful. SecOff A> CREATE CONFIG=ROUTER.CFG Info ( ): Operation successful. SecOff A> SET CONFIG=ROUTER.CFG Info ( ): Operation successful.
99 login: manager Password: friend Manager > SET SYSTEM NAME=B Info ( ): Operation successful. Manager B> Manager B> ADD USER=secoff PASSWORD=passwdSB PRIVILEGE=SECURITYOFFICER User Authentication Database Username: secoff () Status: enabled Privilege: Sec Off Telnet: no Login: yes Logins: 0 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails: Manager B> CREATE PPP=0 OVER=eth0-any Info ( ): Operation successful. Manager B> SET PPP=0 OVER=eth0-any BAP=OFF [email protected] PASS- WORD=passwd_b LQR=OFF ECHO=ON Info ( ): Operation successful. Manager B> ENABLE IP Info ( ): IP module has been enabled. Manager B> ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager B> ADD IP INT=ppp0 IP= MASK= Info ( ): interface successfully added. Manager B> ADD IP ROUTE= INT=ppp0 NEXTHOP= Info ( ): IP route successfully added. Manager B> ENABLE FIREWALL Info ( ): 19-Apr :55:22 Firewall enabled.
100 Manager B> CREATE FIREWALL POLICY=net Manager B> ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH Manager B> DISABLE FIREWALL POLICY=net IDENTPROXY Manager B> ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE Manager B> ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC Manager B> ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 Manager B> ADD FIREWALL POLICY=net RU=1 AC=ALLOW INT=ppp0 PROT=UDP GBLPO=500 GBLIP= PO=500 IP= Manager B> ADD FIREWALL POLICY=net RU=2 AC=NONAT INT=vlan1 PROT=ALL IP= Manager B> SET FIREWALL POLICY=net RU=2 REMOTEIP= Manager B> ADD FIREWALL POLICY=net RU=3 AC=NONAT INT=ppp0 PROT=ALL IP= ENCAP=IPSEC
101 Manager B> CREATE ENCO KEY=1 TYPE=GENERAL VALUE="secret" Info ( ): Operation successful. Manager B> CREATE IPSEC POLICY="isa" INT=ppp0 ACTION=PERMIT LPORT=500 RPORT=500 TRANSPORT=UDP Info ( ): Operation successful. Manager B> CREATE ISAKMP POLICY="i" PEER= KEY=1 SENDN=TRUE Manager B> CREATE IPSEC POLICY="vpn" INT=ppp0 ACTION=IPSEC KEYMAN=ISAKMP BUNDLE=1 PEER= Info ( ): Operation successful. Manager B> CREATE IPSEC SASPEC=1 KEYMAN=ISAKMP PROTOCOL=ESP ENCALG=DES HASHALG=SHA Info ( ): Operation successful. Manager B> SET IPSEC POLICY="vpn" LAD= LMA= RAD= RMA= Info ( ): Operation successful. Manager B> CREATE IPSEC BUNDLE=1 KEYMAN=ISAKMP STRING="1" Info ( ): Operation successful. Manager B> CREATE IPSEC POLICY="inet" INT=ppp0 ACTION=PERMIT Info ( ): Operation successful.
102 Manager B> ENABLE IPSEC Info ( ): Operation successful. Manager B> ENABLE ISAKMP Info ( ): ISAKMP has been enabled. Manager B> LOGIN secoff Password: passwdsb SecOff B> ENABLE SYSTEM SECURITY_MODE Info ( ): Operation successful. SecOff A> CREATE CONFIG=ROUTER.CFG Info ( ): Operation successful. SecOff A> SET CONFIG=ROUTER.CFG 1 SET SYSTEM NAME=A 2 ADD USER=secoff PASSWORD=passwdSA PRIVILEGE=SECURITYOFFICER 3 CREATE PPP=0 OVER=eth0-any 4 SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON [email protected] PASSWORD=passwd_a LQR=OFF ECHO=ON 5 ENABLE IP 6 ENABLE IP REMOTEASSIGN 7 ADD IP INT=eth1 IP= MASK= ADD IP INT=vlan1 IP= MASK= ADD IP INT=ppp0-0 IP= ADD IP INT=ppp0-1 IP= MASK= ADD IP ROUTE= INT=ppp0-1 NEXTHOP= ENABLE FIREWALL 13 CREATE FIREWALL POLICY=net 14 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH 15 DISABLE FIREWALL POLICY=net IDENTPROXY 16 ADD FIREWALL POLICY=net INT=eth1 TYPE=PRIVATE 17 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 18 ADD FIREWALL POLICY=net INT=ppp0-0 TYPE=PUBLIC 19 ADD FIREWALL POLICY=net INT=ppp0-1 TYPE=PUBLIC 20 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0-1 GBLIP= ADD FIREWALL POLICY=net RULE=1 AC=ALLOW INT=ppp0-1 PROTO=TCP IP= PORT=80 Info ( ): Operation successful.
103 22 ADD FIREWALL POLICY=net RULE=2 AC=ALLOW INT=ppp0-1 PROTO=TCP IP= PORT=25 23 ADD FIREWALL POLICY=net RULE=3 AC=ALLOW INT=ppp0-1 PROTO=TCP IP= PORT=53 24 ADD FIREWALL POLICY=net RULE=4 AC=ALLOW INT=ppp0-1 PROTO=UDP IP= PORT=53 25 ADD FIREWALL POLICY=net RU=5 AC=ALLOW INT=ppp0-1 PROTO=UDP GBLPO=500 GBLIP= PO=500 IP= ADD FIREWALL POLICY=net RU=6 AC=NONAT INT=vlan1 PROT=ALL IP= SET FIREWALL POLICY=net RU=6 REMOTEIP= ADD FIREWALL POLICY=net RU=7 AC=NONAT INT=ppp0-1 PROT=ALL IP= ENCAP=IPSEC 29 CREATE ISAKMP POLICY="i" PEER= KEY=1 SENDN=TRUE 30 CREATE IPSEC SASPEC=1 KEYMAN=ISAKMP PROTOCOL=ESP ENCALG=DES HASHALG=SHA 31 CREATE IPSEC BUNDLE=1 KEYMAN=ISAKMP STRING="1" 32 CREATE IPSEC POLICY="isa" INT=ppp0-1 ACTION=PERMIT LPORT=500 RPORT=500 TRANSPORT=UDP 33 CREATE IPSEC POLICY="vpn" INT=ppp0-1 ACTION=IPSEC KEYMAN=ISAKMP BUNDLE=1 PEER= SET IPSEC POLICY="vpn" LAD= LMA= RAD= RMA= CREATE IPSEC POLICY="inet" INT=ppp0-1 ACTION=PERMIT 36 ENABLE IPSEC 37 ENABLE ISAKMP 1 SET SYSTEM NAME=B 2 ADD USER=secoff PASSWORD=passwdSB PRIVILEGE=SECURITYOFFICER 3 CREATE PPP=0 OVER=eth0-any 4 SET PPP=0 OVER=eth0-any BAP=OFF [email protected] PASSWORD=passwd_b LQR=OFF ECHO=ON 5 ENABLE IP 6 ADD IP INT=vlan1 IP= MASK= ADD IP INT=ppp0 IP= MASK= ADD IP ROUTE= INT=ppp0 NEXTHOP= ENABLE FIREWALL 10 CREATE FIREWALL POLICY=net 11 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH 12 DISABLE FIREWALL POLICY=net IDENTPROXY 13 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 14 ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC 15 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 16 ADD FIREWALL POLICY=net RU=1 AC=ALLOW INT=ppp0 PROT=UDP GBLPO=500 GBLIP= PO=500 IP= ADD FIREWALL POLICY=net RU=2 AC=NONAT INT=vlan1 PROT=ALL IP= SET FIREWALL POLICY=net RU=2 REMOTEIP= ADD FIREWALL POLICY=net RU=3 AC=NONAT INT=ppp0 PROT=ALL IP= ENCAP=IPSEC 20 CREATE ISAKMP POLICY="i" PEER= KEY=1 SENDN=TRUE 21 CREATE IPSEC SASPEC=1 KEYMAN=ISAKMP PROTOCOL=ESP ENCALG=DES HASHALG=SHA 22 CREATE IPSEC BUNDLE=1 KEYMAN=ISAKMP STRING="1" 23 CREATE IPSEC POLICY="isa" INT=ppp0 ACTION=PERMIT LPORT=500 RPORT=500 TRANSPORT=UDP 24 CREATE IPSEC POLICY="vpn" INT=ppp0 ACTION=IPSEC KEYMAN=ISAKMP BUNDLE=1 PEER= SET IPSEC POLICY="vpn" LAD= LMA= RAD= RMA= CREATE IPSEC POLICY="inet" INT=ppp0 ACTION=PERMIT 27 ENABLE IPSEC 28 ENABLE ISAKMP
104
105 IP :
106 login: manager Password: friend Manager > SET SYSTEM NAME=A Info ( ): Operation successful. Manager A> Manager A> ADD USER=secoff PASSWORD=passwdSA PRIVILEGE=SECURITYOFFICER User Authentication Database Username: secoff () Status: enabled Privilege: Sec Off Telnet: no Login: yes Logins: 0 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails: Manager A> CREATE PPP=0 OVER=eth0-any Info ( ): Operation successful. Manager A> SET PPP=0 OVER=eth0-any BAP=OFF [email protected] PASSWORD=passwd_a LQR=OFF ECHO=ON Info ( ): Operation successful. Manager A> ENABLE IP Info ( ): IP module has been enabled.
107 Manager A> ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager A> ADD IP INT=ppp0 IP= MASK= Info ( ): interface successfully added. Manager A> ADD IP ROUTE= INT=ppp0 NEXTHOP= Info ( ): IP route successfully added. Manager A> ENABLE FIREWALL Info ( ): 19-Apr :55:22 Firewall enabled. Manager A> CREATE FIREWALL POLICY=net Manager A> ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACHABLE Manager A> DISABLE FIREWALL POLICY=net IDENTPROXY Manager A> ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE Manager A> ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC Manager A> ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 Manager A> ADD FIREWALL POLICY=net RU=1 AC=ALLOW INT=ppp0 PROTO=UDP GBLPO=500 GBLIP= PO=500 IP=
108 Manager A> ADD FIREWALL POLICY=net RU=2 AC=NONAT INT=vlan1 PROT=ALL IP= Manager A> SET FIREWALL POLICY=net RU=2 REMOTEIP= Manager A> CREATE ENCO KEY=1 TYPE=GENERAL VALUE="secret-ab" Info ( ): Operation successful. Manager A> CREATE ENCO KEY=2 TYPE=GENERAL VALUE="secret-ac" Info ( ): Operation successful. Manager A> ADD FIREWALL POLICY=net RU=3 AC=NONAT INT=vlan1 PROT=ALL IP= Manager A> SET FIREWALL POLICY=net RU=3 REMOTEIP= Manager A> ADD FIREWALL POLICY=net RU=4 AC=NONAT INT=ppp0 PROT=ALL IP= ENCAP=IPSEC Manager A> CREATE ISAKMP POLICY="i_B" PEER=ANY KEY=1 SENDN=TRUE REMOTEID="client_B" MODE=AGGRESSIVE HEARTBEATMODE=BOTH Info ( ): Operation successful. Manager A> CREATE ISAKMP POLICY="i_C" PEER=ANY KEY=2 SENDN=TRUE REMOTEID="client_C" MODE=AGGRESSIVE HEARTBEATMODE=BOTH Info ( ): Operation successful.
109 Manager A> CREATE IPSEC SASPEC=1 KEYMAN=ISAKMP PROTOCOL=ESP ENCALG=DES HASHALG=SHA Info ( ): Operation successful. Manager A> CREATE IPSEC BUNDLE=1 KEYMAN=ISAKMP STRING="1" Info ( ): Operation successful. Manager A> CREATE IPSEC POLICY="isa" INT=ppp0 ACTION=PERMIT LPORT=500 RPORT=500 TRANSPORT=UDP Info ( ): Operation successful. Manager A> CREATE IPSEC POLICY="vpn_B" INT=ppp0 ACTION=IPSEC KEYMAN=ISAKMP BUN- DLE=1 PEER=DYNAMIC Info ( ): Operation successful. Manager A> CREATE IPSEC POLICY="vpn_C" INT=ppp0 ACTION=IPSEC KEYMAN=ISAKMP BUN- DLE=1 PEER=DYNAMIC Info ( ): Operation successful. Manager A> SET IPSEC POLICY="vpn_B" LAD= LMA= RAD= RMA= Info ( ): Operation successful. Manager A> SET IPSEC POLICY="vpn_C" LAD= LMA= RAD= RMA= Info ( ): Operation successful. Manager A> CREATE IPSEC POLICY="inet" INT=ppp0 ACTION=PERMIT Info ( ): Operation successful. Manager A> ENABLE IPSEC Info ( ): Operation successful. Manager A> ENABLE ISAKMP Info ( ): ISAKMP has been enabled. Manager A> LOGIN secoff Password: passwdsa SecOff A> ENABLE SYSTEM SECURITY_MODE Info ( ): Operation successful.
110 SecOff A> CREATE CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager > SET SYSTEM NAME=C Info ( ): Operation successful. Manager C> SecOff A> SET CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager B> ADD USER=secoff PASSWORD=passwdSB PRIVILEGE=SECURITYOFFICER User Authentication Database Username: secoff () Status: enabled Privilege: Sec Off Telnet: no Login: yes Logins: 0 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails: login: manager Password: friend Manager C> ADD USER=secoff PASSWORD=passwdSC PRIVILEGE=SECURITYOFFICER User Authentication Database Username: secoff () Status: enabled Privilege: Sec Off Telnet: no Login: yes Logins: 0 Fails: 0 Sent: 0 Rcvd: 0 Authentications: 0 Fails: Manager > SET SYSTEM NAME=B Info ( ): Operation successful. Manager B> Manager B> CREATE PPP=0 OVER=eth0-any Info ( ): Operation successful.
111 Manager B> SET PPP=0 OVER=eth0-any BAP=OFF PASS- WORD=passwd_b IPREQUESRT=ON LQR=OFF ECHO=ON Info ( ): Operation successful. Manager C> SET PPP=0 OVER=eth0-any BAP=OFF PASS- WORD=passwd_c IPREQUESRT=ON LQR=OFF ECHO=ON Info ( ): Operation successful. Manager B> ENABLE IP Info ( ): IP module has been enabled. Manager B> ENABLE IP REMOTEASSIGN Info ( ): IP module has been enabled. Manager B> ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager C> ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager B> ADD IP INT=ppp0 IP= Info ( ): interface successfully added. Manager B> ADD IP ROUTE= INT=ppp0 NEXTHOP= Info ( ): IP route successfully added. Manager B> ENABLE FIREWALL Info ( ): 19-Apr :55:22 Firewall enabled. Manager B> CREATE FIREWALL POLICY=net Manager B> ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACHABLE Manager B> DISABLE FIREWALL POLICY=net IDENTPROXY
112 Manager B> ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE Manager B> ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC Manager B> ADD FIREWALL POLICY=net RU=2 AC=NONAT INT=ppp0 PROT=ALL IP= ENCAP=IPSEC Manager C> ADD FIREWALL POLICY=net RU=2 AC=NONAT INT=ppp0 PROT=ALL IP= ENCAP=IPSEC Manager B> ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 Manager B> ADD FIREWALL POLICY=net RU=1 AC=NONAT INT=vlan1 PROT=ALL IP= Manager B> SET FIREWALL POLICY=net RU=1 REMOTEIP= Manager B> CREATE ENCO KEY=1 TYPE=GENERAL VALUE="secret-ab" Info ( ): Operation successful. Manager C> CREATE ENCO KEY=1 TYPE=GENERAL VALUE="secret-ac" Info ( ): Operation successful. Manager C> ADD FIREWALL POLICY=net RU=1 AC=NONAT INT=vlan1 PROT=ALL IP= Manager C> SET FIREWALL POLICY=net RU=1 REMOTEIP=
113 Manager B> CREATE ISAKMP POLICY="i_A" PEER= KEY=1 SENDN=TRUE LOCALID="client_B" MODE=AGGRESSIVE HEART- BEATMODE=BOTH Manager C> CREATE ISAKMP POLICY="i_A" PEER= KEY=1 SENDN=TRUE LOCALID="client_C" MODE=AGGRESSIVE HEART- BEATMODE=BOTH Manager B> CREATE IPSEC POLICY="vpn_A" INT=ppp0 ACTION=IPSEC KEYMAN=ISAKMP BUN- DLE=1 PEER= Info ( ): Operation successful. Manager B> SET IPSEC POLICY="vpn_A" LAD= LMA= RAD= RMA= Info ( ): Operation successful. Manager B> CREATE IPSEC SASPEC=1 KEYMAN=ISAKMP PROTOCOL=ESP ENCALG=DES HASHALG=SHA Info ( ): Operation successful. Manager B> CREATE IPSEC BUNDLE=1 KEYMAN=ISAKMP STRING="1" Info ( ): Operation successful. Manager B> CREATE IPSEC POLICY="isa" INT=ppp0 ACTION=PERMIT LPORT=500 RPORT=500 TRANSPORT=UDP Info ( ): Operation successful. Manager C> SET IPSEC POLICY="vpn_A" LAD= LMA= RAD= RMA= Info ( ): Operation successful. Manager B> CREATE IPSEC POLICY="inet" INT=ppp0 ACTION=PERMIT Info ( ): Operation successful. Manager B> ENABLE IPSEC Info ( ): Operation successful.
114 Manager B> ENABLE ISAKMP Info ( ): ISAKMP has been enabled. Manager B> LOGIN secoff Password: passwdsb Manager C> LOGIN secoff Password: passwdsc SecOff B> ENABLE SYSTEM SECURITY_MODE Info ( ): Operation successful. SecOff B> CREATE CONFIG=ROUTER.CFG Info ( ): Operation successful. SecOff B> SET CONFIG=ROUTER.CFG Info ( ): Operation successful.
115 1 SET SYSTEM NAME=A 2 ADD USER=secoff PASSWORD=passwdSA PRIVILEGE=SECURITYOFFICER 3 CREATE PPP=0 OVER=eth0-any 4 SET PPP=0 OVER=eth0-any BAP=OFF [email protected] PASSWORD=passwd_a LQR=OFF ECHO=ON 5 ENABLE IP 6 ADD IP INT=vlan1 IP= MASK= ADD IP INT=ppp0 IP= MASK= ADD IP ROUTE= INT=ppp0 NEXTHOP= ENABLE FIREWALL 10 CREATE FIREWALL POLICY=net 11 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACHABLE 12 DISABLE FIREWALL POLICY=net IDENTPROXY 13 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 14 ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC 15 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 16 ADD FIREWALL POLICY=net RU=1 AC=ALLOW INT=ppp0 PROTO=UDP GBLPO=500 GBLIP= PO=500 IP= ADD FIREWALL POLICY=net RU=2 AC=NONAT INT=vlan1 PROT=ALL IP= SET FIREWALL POLICY=net RU=2 REMOTEIP= ADD FIREWALL POLICY=net RU=3 AC=NONAT INT=vlan1 PROT=ALL IP= SET FIREWALL POLICY=net RU=3 REMOTEIP= ADD FIREWALL POLICY=net RU=4 AC=NONAT INT=ppp0 PROT=ALL IP= ENCAP=IPSEC 22 CREATE ISAKMP POLICY="i_B" PEER=ANY KEY=1 SENDN=TRUE REMOTEID="client_B" MODE=AGGRESSIVE HEARTBEATMODE=BOTH 23 CREATE ISAKMP POLICY="i_C" PEER=ANY KEY=2 SENDN=TRUE REMOTEID="client_C" MODE=AGGRESSIVE HEARTBEATMODE=BOTH 24 CREATE IPSEC SASPEC=1 KEYMAN=ISAKMP PROTOCOL=ESP ENCALG=DES HASHALG=SHA 25 CREATE IPSEC BUNDLE=1 KEYMAN=ISAKMP STRING="1" 26 CREATE IPSEC POLICY="isa" INT=ppp0 ACTION=PERMIT LPORT=500 RPORT=500 TRANSPORT=UDP 27 CREATE IPSEC POLICY="vpn_B" INT=ppp0 ACTION=IPSEC KEYMAN=ISAKMP BUNDLE=1 PEER=DYNAMIC 28 CREATE IPSEC POLICY="vpn_C" INT=ppp0 ACTION=IPSEC KEYMAN=ISAKMP BUNDLE=1 PEER=DYNAMIC 29 SET IPSEC POLICY="vpn_B" LAD= LMA= RAD= RMA= SET IPSEC POLICY="vpn_C" LAD= LMA= RAD= RMA= CREATE IPSEC POLICY="inet" INT=ppp0 ACTION=PERMIT 32 ENABLE IPSEC 33 ENABLE ISAKMP
116 1 SET SYSTEM NAME=B 2 ADD USER=secoff PASSWORD=passwdSB PRIVILEGE=SECURITYOFFICER 3 CREATE PPP=0 OVER=eth0-any 4 SET PPP=0 OVER=eth0-any BAP=OFF [email protected] PASSWORD=passwd_b LQR=OFF ECHO=ON 5 ENABLE IP 6 ENABLE IP REMOTEASSIGN 7 ADD IP INT=vlan1 IP= MASK= ADD IP INT=ppp0 IP= ADD IP ROUTE= INT=ppp0 NEXTHOP= ENABLE FIREWALL 11 CREATE FIREWALL POLICY=net 12 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACHABLE 13 DISABLE FIREWALL POLICY=net IDENTPROXY 14 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 15 ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC 16 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 17 ADD FIREWALL POLICY=net RU=1 AC=NONAT INT=vlan1 PROT=ALL IP= SET FIREWALL POLICY=net RU=1 REMOTEIP= ADD FIREWALL POLICY=net RU=2 AC=NONAT INT=ppp0 PROT=ALL IP= ENCAP=IPSEC 20 CREATE ISAKMP POLICY="i_A" PEER= KEY=1 SENDN=TRUE LOCALID="client_B" MODE=AGGRESSIVE HEARTBEATMODE=BOTH 21 CREATE IPSEC SASPEC=1 KEYMAN=ISAKMP PROTOCOL=ESP ENCALG=DES HASHALG=SHA 22 CREATE IPSEC BUNDLE=1 KEYMAN=ISAKMP STRING="1" 23 CREATE IPSEC POLICY="isa" INT=ppp0 ACTION=PERMIT LPORT=500 RPORT=500 TRANSPORT=UDP 24 CREATE IPSEC POLICY="vpn_A" INT=ppp0 ACTION=IPSEC KEYMAN=ISAKMP BUNDLE=1 PEER= SET IPSEC POLICY="vpn_A" LAD= LMA= RAD= RMA= CREATE IPSEC POLICY="inet" INT=ppp0 ACTION=PERMIT 27 ENABLE IPSEC 28 ENABLE ISAKMP
117 1 SET SYSTEM NAME=C 2 ADD USER=secoff PASSWORD=passwdSC PRIVILEGE=SECURITYOFFICER 3 CREATE PPP=0 OVER=eth0-any 4 SET PPP=0 OVER=eth0-any BAP=OFF [email protected] PASSWORD=passwd_c IPREQUEST=ON LQR=OFF ECHO=ON 5 ENABLE IP 6 ENABLE IP REMOTEASSIGN 7 ADD IP INT=vlan1 IP= MASK= ADD IP INT=ppp0 IP= ADD IP ROUTE= INT=ppp0 NEXTHOP= ENABLE FIREWALL 11 CREATE FIREWALL POLICY=net 12 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACHABLE 13 DISABLE FIREWALL POLICY=net IDENTPROXY 14 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 15 ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC 16 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 17 ADD FIREWALL POLICY=net RU=1 AC=NONAT INT=vlan1 PROT=ALL IP= SET FIREWALL POLICY=net RU=1 REMOTEIP= ADD FIREWALL POLICY=net RU=2 AC=NONAT INT=ppp0 PROT=ALL IP= ENCAP=IPSEC 20 CREATE ISAKMP POLICY="i_A" PEER= KEY=1 SENDN=TRUE LOCALID="client_C" MODE=AGGRESSIVE HEARTBEATMODE=BOTH 21 CREATE IPSEC SASPEC=1 KEYMAN=ISAKMP PROTOCOL=ESP ENCALG=DES HASHALG=SHA 22 CREATE IPSEC BUNDLE=1 KEYMAN=ISAKMP STRING="1" 23 CREATE IPSEC POLICY="isa" INT=ppp0 ACTION=PERMIT LPORT=500 RPORT=500 TRANSPORT=UDP 25 CREATE IPSEC POLICY="vpn_A" INT=ppp0 ACTION=IPSEC KEYMAN=ISAKMP BUNDLE=1 PEER= SET IPSEC POLICY="vpn_A" LAD= LMA= RAD= RMA= CREATE IPSEC POLICY="inet" INT=ppp0 ACTION=PERMIT 28 ENABLE IPSEC 29 ENABLE ISAKMP
118
119 login: manager Password: friend Manager > CREATE PPP=0 OVER=eth0-any Info ( ): Operation successful. Manager > SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON PASSWORD=passwd_a LQR=OFF ECHO=ON Info ( ): Operation successful. Manager > CREATE PPP=1 OVER=eth0-any Info ( ): Operation successful. Manager > SET PPP=1 OVER=eth0-any BAP=OFF IPREQUEST=ON USER=flets_a PASSWORD=fpasswd_a LQR=OFF ECHO=ON Info ( ): Operation successful. Manager > ENABLE IP Info ( ): IP module has been enabled. Manager > ENABLE IP REMOTEASSIGN Info ( ): Remote IP assignment has been enabled. Manager > ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added.
120 Manager > ADD IP INT=ppp0 IP= Info ( ): interface successfully added. Manager > CREATE FIREWALL POLICY=net Manager > ADD IP INT=ppp1 IP= Info ( ): interface successfully added. Manager > ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH Manager > ADD IP ROUTE= INT=ppp0 NEXTHOP= Info ( ): IP route successfully added. Manager > ADD IP ROUTE= MASK= INT=ppp1 NEXTHOP= Info ( ): IP route successfully added. Manager > ENABLE IP DNSRELAY Info ( ): Operation successful. Manager > DISABLE FIREWALL POLICY=net IDENTPROXY Manager > ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE Manager > ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC Manager > ENABLE FIREWALL Info ( ): 19-Apr :55:22 Firewall enabled.
121 Manager > ADD FIREWALL POLICY=net INT=ppp1 TYPE=PUBLIC Manager > ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 Manager > ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp1 Manager > SET PASSWORD Old password: friend New password: xxxxxxx Confirm: xxxxxxx Manager > CREATE CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager > SET CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager > SHOW PPP Name Enabled ifindex Over CP State ppp0 YES 04 IPCP OPENED eth0-any LCP OPENED ppp1 YES 04 IPCP OPENED eth0-any LCP OPENED Manager > ADD FIREWALL POLICY=net RU=1 AC=ALLOW INT=ppp1 PROT=tcp PORT=80 IP= GBLINT= GBLP=80 Manager > SET TIME=01:00:01 DATE=01-APR-2005 System time is 01:00:01 on Sunday 01-APR-2005.
122 1 CREATE PPP=0 OVER=eth0-any 2 SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON [email protected] PASSWORD=passwd_a LQR=OFF ECHO=ON 3 CREATE PPP=1 OVER=eth0-any 4 SET PPP=1 OVER=eth0-any BAP=OFF IPREQUEST=ON USER=flets_a PASSWORD=fpasswd_a LQR=OFF ECHO=ON 5 ENABLE IP 6 ENABLE IP REMOTEASSIGN 7 ADD IP INT=vlan1 IP= MASK= ADD IP INT=ppp0 IP= ADD IP INT=ppp1 IP= ADD IP ROUTE= INT=ppp0 NEXTHOP= ADD IP ROUTE= MASK= INT=ppp1 NEXTHOP= ENABLE IP DNSRELAY 13 ENABLE FIREWALL 14 CREATE FIREWALL POLICY=net 15 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACHABLE 16 DISABLE FIREWALL POLICY=net IDENTPROXY 17 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 18 ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC 19 ADD FIREWALL POLICY=net INT=ppp1 TYPE=PUBLIC 20 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 21 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp1 22 ADD FIREWALL POLICY=net RU= 1 AC=ALLOW INT=ppp1 PROT=tcp PORT=80 IP= GBLIP= GBLP=80
123 login: manager Password: friend
124 Manager > CREATE PPP=0 OVER=eth0-any Info ( ): Operation successful. Manager > SET PPP=1 OVER=eth0-any BAP=OFF IPREQUEST=ON USER=flets_a PASSWORD=fpasswd_a LQR=OFF ECHO=ON Info ( ): Operation successful. Manager > SET PPP=1 OVER=eth0-any BAP=OFF IPREQUEST=ON USER=flets_b PASSWORD=fpasswd_b LQR=OFF ECHO=ON Info ( ): Operation successful. Manager > SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON PASSWORD=passwd_a LQR=OFF ECHO=ON Manager > ENABLE IP Info ( ): IP module has been enabled. Info ( ): Operation successful. Manager > SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON PASSWORD=passwd_b LQR=OFF ECHO=ON Info ( ): Operation successful. Manager > CREATE PPP=1 OVER=eth0-any Info ( ): Operation successful. Manager > ENABLE IP REMOTEASSIGN Info ( ): Remote IP assignment has been enabled. Manager > ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager > ADD IP INT=vlan1 IP= MASK= Info ( ): interface successfully added. Manager > ADD IP INT=ppp0 IP= Info ( ): interface successfully added.
125 Manager > ADD IP INT=ppp1 IP= Info ( ): interface successfully added. Manager > CREATE FIREWALL POLICY=net Manager > ADD IP ROUTE= INT=ppp0 NEXTHOP= Info ( ): IP route successfully added. Manager > ADD IP ROUTE= MASK= INT=ppp1 NEXTHOP= Info ( ): IP route successfully added. Manager > ADD IP ROUTE= MASK= INT=ppp1 NEXTHOP= Info ( ): IP route successfully added. Manager > ENABLE IP DNSRELAY Info ( ): Operation successful. Manager > ENABLE FIREWALL Info ( ): 19-Apr :55:22 Firewall enabled. Manager > ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACH Manager > DISABLE FIREWALL POLICY=net IDENTPROXY Manager > ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE Manager > ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC
126 Manager > ADD FIREWALL POLICY=net INT=ppp1 TYPE=PUBLIC Manager > ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 Manager > SET PASSWORD Old password: friend New password: xxxxxxx Confirm: xxxxxxx Manager > CREATE CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager > SET CONFIG=ROUTER.CFG Info ( ): Operation successful. Manager > ADD FIREWALL POLICY=net RULE=1 AC=ALLOW INT=ppp1 PROT=ALL REMOTEIP= Manager > ADD FIREWALL POLICY=net RULE=1 AC=ALLOW INT=ppp1 PROT=ALL REMOTEIP= Manager > SET TIME=01:00:01 DATE=01-APR-2005 Manager > SHOW PPP Name Enabled ifindex Over CP State ppp0 YES 04 IPCP OPENED eth0-any LCP OPENED ppp1 YES 04 IPCP OPENED eth0-any LCP OPENED System time is 01:00:01 on Sunday 01-APR-2005.
127 1 CREATE PPP=0 OVER=eth0-any 2 SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON [email protected] PASSWORD=passwd_a LQR=OFF ECHO=ON 3 CREATE PPP=1 OVER=eth0-any 4 SET PPP=1 OVER=eth0-any BAP=OFF IPREQUEST=ON USER=flets_a PASSWORD=fpasswd_a LQR=OFF ECHO=ON 5 ENABLE IP 6 ENABLE IP REMOTEASSIGN 7 ADD IP INT=vlan1 IP= MASK= ADD IP INT=ppp0 IP= ADD IP INT=ppp1 IP= ADD IP ROUTE= INT=ppp0 NEXTHOP= ADD IP ROUTE= MASK= INT=ppp1 NEXTHOP= ENABLE IP DNSRELAY 13 ENABLE FIREWALL 14 CREATE FIREWALL POLICY=net 15 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACHABLE 16 DISABLE FIREWALL POLICY=net IDENTPROXY 17 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 18 ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC 19 ADD FIREWALL POLICY=net INT=ppp1 TYPE=PUBLIC 20 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 21 ADD FIREWALL POLICY=net RULE=1 AC=ALLOW INT=ppp1 PROT=ALL REMOTEIP= CREATE PPP=0 OVER=eth0-any 2 SET PPP=0 OVER=eth0-any BAP=OFF IPREQUEST=ON [email protected] PASSWORD=passwd_b LQR=OFF ECHO=ON 3 CREATE PPP=1 OVER=eth0-any 4 SET PPP=1 OVER=eth0-any BAP=OFF IPREQUEST=ON USER=flets_b PASSWORD=fpasswd_b LQR=OFF ECHO=ON 5 ENABLE IP 6 ENABLE IP REMOTEASSIGN 7 ADD IP INT=vlan1 IP= MASK= ADD IP INT=ppp0 IP= ADD IP INT=ppp1 IP= ADD IP ROUTE= INT=ppp0 NEXTHOP= ADD IP ROUTE= MASK= INT=ppp1 NEXTHOP= ENABLE IP DNSRELAY 13 ENABLE FIREWALL 14 CREATE FIREWALL POLICY=net 15 ENABLE FIREWALL POLICY=net ICMP_F=PING,UNREACHABLE 16 DISABLE FIREWALL POLICY=net IDENTPROXY 17 ADD FIREWALL POLICY=net INT=vlan1 TYPE=PRIVATE 18 ADD FIREWALL POLICY=net INT=ppp0 TYPE=PUBLIC 19 ADD FIREWALL POLICY=net INT=ppp1 TYPE=PUBLIC 20 ADD FIREWALL POLICY=net NAT=ENHANCED INT=vlan1 GBLINT=ppp0 21 ADD FIREWALL POLICY=net RULE=1 AC=ALLOW INT=ppp1 PROT=ALL REMOTEIP=
128 Manager > DISABLE PPP=0 Info ( ): Operation successful. Manager > SHOW PPP Name Enabled ifindex Over CP State ppp0 NO 04 IPCP CLOSED eth0-any LCP INITIAL Manager > SHOW CONFIG DYN=PPP # # PPP configuration # create ppp=0 over=eth0-any set ppp=0 bap=off iprequest=on username="user1@isp" password="isppasswd1" set ppp=0 over=eth0-any lqr=off echo=10 disable ppp=0 ADD IP INT=ppp0-0 IP= ADD IP INT=ppp0-1 IP= MASK= ADD IP INT=VLAN1 IP= MASK= ADD IP ROUTE= INT=ppp0-1 NEXT= Manager > RESTART ROUTER
129
130
131
132
133 Microsoft Telnet> set term vt100 Microsoft Telnet> set bsasdel Microsoft Telnet> set codeset Shift JIS Microsoft Telnet> display Microsoft Telnet> quit
134
135
136
137 PIN 1 PIN 1 1 TD+ 2 TD- 3 RD+ 6 RD- 1 TD+ 2 TD- 3 RD+ 6 RD- 1TD+ 2TD- TD+ 1 TD- 2 RD+ 3 RD- 6 TD+ 1 TD- 2 RD+ 3 RD- 6 TD+1 TD-2 3RD+ 6RD- 1TD+ 2TD- RD+3 RD-6 TD+ 1 TD- 2 3RD+ 6RD- RD+ 3 RD- 6
138 Manager > SHOW SYSTEM Router System Status Time 01:36:14 Date 05-Apr Board ID Bay Board Name Host Id Rev Serial number Base 257 AR570S 0 M2-0 D A PIC 75 0 AT-AR PIC E1/T1 PRI 0 M Memory - DRAM : kb FLASH : kb Chip Revisions
139 D Data B Data PRI E1T1 Active NT
140 PIN 1 PIN 1 D Data B Data PRI E1T1 Active NT
141 D Data B Data PRI E1T1 Active NT B1 B2 BRI S/T ACT D
142 B1 B2 B1 B2 BRI BRI S/T S/T ACT D ACT D B1 B2 BRI S/T ACT D
143
144
145 S/N Rev 1A login: manager Password: xxxxxxx Manager >SHOW SYSTEM Router System Status Time 01:36:14 Date 05-Apr Board ID Bay Board Name Host Id Rev Serial number Base 257 AR570S 0 M2-0 D A PIC 75 0 AT-AR PIC E1/T1 PRI 0 M Memory - DRAM : kb FLASH : kb Chip Revisions SysDescription CentreCOM AR570S version B Mar-2006 SysContact SysLocation SysName OSAKA SysDistName SysUpTime ( 00:11:25 ) Boot Image : fbr size Mar-2006 Software Version: B Mar-2006 Release Version : B Oct
146
147
148
CentreCOM AR550S 取扱説明書 Rev.B
 *J613-M0710-00=B* J613-M0710-00 Rev.B 050506 AR550S 100~240V Manager > HELP AR550S - V2.7 Rev.01 2005/03/23 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" (# ) Help Operation
*J613-M0710-00=B* J613-M0710-00 Rev.B 050506 AR550S 100~240V Manager > HELP AR550S - V2.7 Rev.01 2005/03/23 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" (# ) Help Operation
CentreCOM AR450S 取扱説明書
 AR450S Broadband Router 100~240V Manager > HELP AR450 - V2.5 Rev.01 2003/05/06 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" Help Operation Help INterface Help Ppp Help
AR450S Broadband Router 100~240V Manager > HELP AR450 - V2.5 Rev.01 2003/05/06 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" Help Operation Help INterface Help Ppp Help
AR410 V2 取扱説明書
 AR410 V2 Broadband Router CentreCOM AR410 V2 100~240V Manager > HELP CentreCOM AR410 V2 - V2.3 Rev.01 2002/09/04 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" * 2002/09
AR410 V2 Broadband Router CentreCOM AR410 V2 100~240V Manager > HELP CentreCOM AR410 V2 - V2.3 Rev.01 2002/09/04 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" * 2002/09
CentreCOM AR560S取扱説明書
 Manager > HELP AR560S - V2.9 Rev.01 2010/02/05 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" (# ) Help Operation Help INterface Help ISdn ISDN Help Tdm Help FRamerelay Help
Manager > HELP AR560S - V2.9 Rev.01 2010/02/05 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" (# ) Help Operation Help INterface Help ISdn ISDN Help Tdm Help FRamerelay Help
AR415S 取扱説明書
 AR415S Manager > HELP AR415S - V2.8 Rev.01 2006/11/09 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" Help Operation Help INterface Help ISdn ISDN Help Tdm Help Ppp PPP
AR415S Manager > HELP AR415S - V2.8 Rev.01 2006/11/09 This online help is written in Japanese (Shift-JIS). "HELP OPERATION" "H O" Help Operation Help INterface Help ISdn ISDN Help Tdm Help Ppp PPP
Soliton Net’Attest EPS + AR router series L2TP+IPsec RADIUS 設定例
 Soliton Net Attest EPS + AR router series L2TP+IPsec RADIUS 設定例 2011/June アライドテレシス株式会社 Revision 1.1 1. Net Attest EPS AR VPN 2 1. 1. 1. AR AR (RADIUS ) 2. 2. Net Attest EPS 3-1. 3-1. iphone/ipad 3-2. 3-2.
Soliton Net Attest EPS + AR router series L2TP+IPsec RADIUS 設定例 2011/June アライドテレシス株式会社 Revision 1.1 1. Net Attest EPS AR VPN 2 1. 1. 1. AR AR (RADIUS ) 2. 2. Net Attest EPS 3-1. 3-1. iphone/ipad 3-2. 3-2.
CentreCOM VX811R 取扱説明書
 *613-000317=B* 613-000317 Rev.B 070131 VX811R a Manager > HELP a Help Help Management Help INterface Help Ppp Help VLan Help Bridge Help IP Help Firewall Help Dhcp Help L2tp Help VDsl Help Confupdate
*613-000317=B* 613-000317 Rev.B 070131 VX811R a Manager > HELP a Help Help Management Help INterface Help Ppp Help VLan Help Bridge Help IP Help Firewall Help Dhcp Help L2tp Help VDsl Help Confupdate
ARルーターバージョンアップ手順書
 P/N J613-M2972-02 Rev.J 110705 1... 3 1.1... 3 1.2... 3 1.3... 4 2... 4 2.1... 4 3... 5 3.1... 5 3.2... 5 3.3... 6 4... 13 4.1... 13 4.2 Feature License... 14... 15... 15... 15 ON OFF 10BASE-T/100BASE-TX
P/N J613-M2972-02 Rev.J 110705 1... 3 1.1... 3 1.2... 3 1.3... 4 2... 4 2.1... 4 3... 5 3.1... 5 3.2... 5 3.3... 6 4... 13 4.1... 13 4.2 Feature License... 14... 15... 15... 15 ON OFF 10BASE-T/100BASE-TX
IP.dvi
 ... 3... 3... 3... 4... 6 VLAN... 6... 6 DHCP... 7... 7... 9... 9... 10... 12 R... 15... 15... 15 ARP... 18... 18 ARP... 18 DNS... 20... 20 DHCP/BOOTP... 21... 21 DHCP... 22 UDP... 23... 23... 23... 26...
... 3... 3... 3... 4... 6 VLAN... 6... 6 DHCP... 7... 7... 9... 9... 10... 12 R... 15... 15... 15 ARP... 18... 18 ARP... 18 DNS... 20... 20 DHCP/BOOTP... 21... 21 DHCP... 22 UDP... 23... 23... 23... 26...
GRE.dvi
 ... 2... 2... 4... 5 IP NAT... 6 NAT... 7... 10... 10 ADD... 11 ADD TUNNEL... 13 DELETE...... 14 DELETE TUNNEL... 15 DISABLE...... 16 ENABLE...... 17 PURGE... 18 RESET... 19 SET... 20 SET TUNNEL... 21
... 2... 2... 4... 5 IP NAT... 6 NAT... 7... 10... 10 ADD... 11 ADD TUNNEL... 13 DELETE...... 14 DELETE TUNNEL... 15 DISABLE...... 16 ENABLE...... 17 PURGE... 18 RESET... 19 SET... 20 SET TUNNEL... 21
FS900S_B
 FS909S FS917S FS909S FS917S 100~240V 4 5 6 7 8 9 10 11 12 1 9 9 L/A S/D FS909S 10BASE-T/100BASE-TX PORTS (AUTO MDI/MDI-X) FS917S 14 FS909SFS917S 15 16 17 18 19 20 21 22 23 24 2 26 27 28 29 30 31 32 3
FS909S FS917S FS909S FS917S 100~240V 4 5 6 7 8 9 10 11 12 1 9 9 L/A S/D FS909S 10BASE-T/100BASE-TX PORTS (AUTO MDI/MDI-X) FS917S 14 FS909SFS917S 15 16 17 18 19 20 21 22 23 24 2 26 27 28 29 30 31 32 3
L2plusスイッチバージョンアップ手順書
 P/N J613-M0005-15 Rev.G 110705 1... 3 1.1... 3 1.2... 3 1.3... 4 2... 4 2.1... 4 3... 5 3.1... 5 3.2... 5 3.3... 6 4... 13 4.1... 13... 14... 14... 14 25 26 L/A 1 C/D L/A 3 C/D L/A 5 C/D L/A 7 C/D L/A
P/N J613-M0005-15 Rev.G 110705 1... 3 1.1... 3 1.2... 3 1.3... 4 2... 4 2.1... 4 3... 5 3.1... 5 3.2... 5 3.3... 6 4... 13 4.1... 13... 14... 14... 14 25 26 L/A 1 C/D L/A 3 C/D L/A 5 C/D L/A 7 C/D L/A
CentreCOM 8724SL/8748SL 取扱説明書 Rev.A
 8724SL 8748SL 100~240V 4 5 6 7 8 Screen displays User Entry 9 10 11 12 1 8748SL 8724SL 14 15 16 8724SL 8748SL 17 18 19 20 21 22 2 24 25 26 8748SL 27 VT-Kit2 28 29 30 3 login: manager a Password: friend
8724SL 8748SL 100~240V 4 5 6 7 8 Screen displays User Entry 9 10 11 12 1 8748SL 8724SL 14 15 16 8724SL 8748SL 17 18 19 20 21 22 2 24 25 26 8748SL 27 VT-Kit2 28 29 30 3 login: manager a Password: friend
CentreCOM 8316XL/8324XL
 8316XL 8324XL 8316XL 8324XL 4 5 6 7 8 9 10 11 12 1 14 8316XL8324XL 8316XL8324XL 8324XL 8316XL 8316XL 15 16 17 18 8324XL8316XL 19 20 21 22 23 24 2 26 27 8316XL 8324XL 28 29 30 31 32 8324XL8316XL 33 34
8316XL 8324XL 8316XL 8324XL 4 5 6 7 8 9 10 11 12 1 14 8316XL8324XL 8316XL8324XL 8324XL 8316XL 8316XL 15 16 17 18 8324XL8316XL 19 20 21 22 23 24 2 26 27 8316XL 8324XL 28 29 30 31 32 8324XL8316XL 33 34
設定例集_Rev.8.03, Rev.9.00, Rev.10.01対応
 Network Equipment 設定例集 Rev.8.03, Rev.9.00, Rev.10.01 対応 2 3 4 5 6 7 8 help > help show command > show command console character administrator pp disable disconnect 9 pp enable save Password: login timer
Network Equipment 設定例集 Rev.8.03, Rev.9.00, Rev.10.01 対応 2 3 4 5 6 7 8 help > help show command > show command console character administrator pp disable disconnect 9 pp enable save Password: login timer
SRT/RTX/RT設定例集
 Network Equipment Rev.6.03, Rev.7.00, Rev.7.01 Rev.8.01, Rev.8.02, Rev.8.03 Rev.9.00, Rev.10.00, Rev.10.01 2 3 4 5 6 1 2 3 1 2 3 7 RTX1000 RTX1000 8 help > help show command > show command console character
Network Equipment Rev.6.03, Rev.7.00, Rev.7.01 Rev.8.01, Rev.8.02, Rev.8.03 Rev.9.00, Rev.10.00, Rev.10.01 2 3 4 5 6 1 2 3 1 2 3 7 RTX1000 RTX1000 8 help > help show command > show command console character
RTX830 取扱説明書
 RTX830 JA 1 2 3 4 5 6 7 8 9 10 11 external-memory performance-test go 12 13 show config 14 15 16 17 18 19 20 save 21 22 23 24 25 26 27 save RTX830 BootROM Ver. 1.00 Copyright (c) 2017 Yamaha Corporation.
RTX830 JA 1 2 3 4 5 6 7 8 9 10 11 external-memory performance-test go 12 13 show config 14 15 16 17 18 19 20 save 21 22 23 24 25 26 27 save RTX830 BootROM Ver. 1.00 Copyright (c) 2017 Yamaha Corporation.
RT300/140/105シリーズ 取扱説明書
 REMOTE & BROADBAND ROUTER RT300i/RT140p/RT140f/RT140i RT140e/RT105p/RT105i/RT105e 2 3 4 5 6 7 8 9 10 Bold face Enter Ctrl Tab BS Del Console RT105i RT300i RT140p RT140f RT140i RT140e RT105p RT105i RT105e
REMOTE & BROADBAND ROUTER RT300i/RT140p/RT140f/RT140i RT140e/RT105p/RT105i/RT105e 2 3 4 5 6 7 8 9 10 Bold face Enter Ctrl Tab BS Del Console RT105i RT300i RT140p RT140f RT140i RT140e RT105p RT105i RT105e
RT300i/RT140x/RT105i 取扱説明書
 2 3 4 5 6 7 8 9 10 Bold face Enter Ctrl Tab BS Del Typewriter face RT105i RT300i RT140p RT140f RT140i RT140e RT105i RT300i 11 RARP 9600 bit/s 8 http://www.rtpro.yamaha.co.jp/ ftp.rtpro.yamaha.co.jp 12
2 3 4 5 6 7 8 9 10 Bold face Enter Ctrl Tab BS Del Typewriter face RT105i RT300i RT140p RT140f RT140i RT140e RT105i RT300i 11 RARP 9600 bit/s 8 http://www.rtpro.yamaha.co.jp/ ftp.rtpro.yamaha.co.jp 12
ヤマハルーターのCLI:Command Line Interface
 (Command Line Interface) cf. http://www.rtpro.yamaha.co.jp/rt/docs/console/ Command Line Interface Graphical User Interface 2 (CLI) WWW(GUI) (CLI) WWW(GUI) character display graphic display keyboard pointer
(Command Line Interface) cf. http://www.rtpro.yamaha.co.jp/rt/docs/console/ Command Line Interface Graphical User Interface 2 (CLI) WWW(GUI) (CLI) WWW(GUI) character display graphic display keyboard pointer
owners.book
 Network Equipment RTX1200 RTX800 2 3 4 5 6 7 8 9 10 bold face Enter Ctrl Tab BS Del Ctrl X Ctrl X Regular face 11 12 13 14 RTX1200 RTX1200 RTX1200 15 16 ), -. / 1 4 5 6 17 18 19 20 21 console character
Network Equipment RTX1200 RTX800 2 3 4 5 6 7 8 9 10 bold face Enter Ctrl Tab BS Del Ctrl X Ctrl X Regular face 11 12 13 14 RTX1200 RTX1200 RTX1200 15 16 ), -. / 1 4 5 6 17 18 19 20 21 console character
conf_example_260V2_260V2_550S_inet+cug_IPsec.pdf
 CUG サービス ( 端末型 ) における 3 点間 IPsecVPN ( インターネットアクセス 支社間通信は本社経由 ) 本社 ( ルーター A:AR550S) と支社 ( ルーター B C:AR260S V2) を CUG(Closed Users Group) サービス (NTT 東日本のフレッツ グループアクセス ( ライト ) および NTT 西日本のフレッツ グループ ( ベーシックメニュー
CUG サービス ( 端末型 ) における 3 点間 IPsecVPN ( インターネットアクセス 支社間通信は本社経由 ) 本社 ( ルーター A:AR550S) と支社 ( ルーター B C:AR260S V2) を CUG(Closed Users Group) サービス (NTT 東日本のフレッツ グループアクセス ( ライト ) および NTT 西日本のフレッツ グループ ( ベーシックメニュー
Net'Attest EPS設定例
 NetAttest EPS 設定例 連携機器 : AR-Router シリーズ Case: ワンタイムパスワードでの認証 Version 1.0 株式会社ソリトンシステムズ NetAttest は 株式会社ソリトンシステムズの登録商標です その他 本書に掲載されている会社名 製品名は それぞれ各社の商標または登録商標です 本文中に は明記していません Copyright 2012, Soliton
NetAttest EPS 設定例 連携機器 : AR-Router シリーズ Case: ワンタイムパスワードでの認証 Version 1.0 株式会社ソリトンシステムズ NetAttest は 株式会社ソリトンシステムズの登録商標です その他 本書に掲載されている会社名 製品名は それぞれ各社の商標または登録商標です 本文中に は明記していません Copyright 2012, Soliton
Microsoft PowerPoint - IPv6セミナーHandsOn編_rev1.1.ppt [互換モード]
![Microsoft PowerPoint - IPv6セミナーHandsOn編_rev1.1.ppt [互換モード] Microsoft PowerPoint - IPv6セミナーHandsOn編_rev1.1.ppt [互換モード]](/thumbs/85/91898466.jpg) SOHO/ 一般ユーザ向けネットワーク [HandsOn 編 ] アライドテレシス株式会社 Task Force on IPv4 Address Exhaustion, Japan 1 Agenda IPv6 オペレータ育成プログラム 物理ネットワーク構成 基本操作 HandsOn1 IPv4 基本設定 HandsOn2 IPv6 ブリッジング HandsOn3 RAによるPrefix 配布 HandsOn4
SOHO/ 一般ユーザ向けネットワーク [HandsOn 編 ] アライドテレシス株式会社 Task Force on IPv4 Address Exhaustion, Japan 1 Agenda IPv6 オペレータ育成プログラム 物理ネットワーク構成 基本操作 HandsOn1 IPv4 基本設定 HandsOn2 IPv6 ブリッジング HandsOn3 RAによるPrefix 配布 HandsOn4
設定例集
 REMOTE ROUTER 1999. 2. 2 YAMAHA NetWare Novell,Inc. INS 64 YAMAHA! M E M O 1 1 1.1 : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 1 1.2 : : : : : : : : : : : : : : : : : : : : :
REMOTE ROUTER 1999. 2. 2 YAMAHA NetWare Novell,Inc. INS 64 YAMAHA! M E M O 1 1 1.1 : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : 1 1.2 : : : : : : : : : : : : : : : : : : : : :
Solution No アライドテレシスコア スイッチ SBx8100 シリーズで実現実現する WAN 型 u-vcf ソリューション 主な目的 複数ロケーションのネットワークを一極集中管理したい ネットワーク管理 / 運用機構の集約によりランニングコストを抑制したい 各ロケーシ
 主な目的 複数ロケーションのネットワークを一極集中管理したい ネットワーク管理 / 運用機構の集約によりランニングコストを抑制したい 各ロケーションにおける現場メンテナンス / リカバリー作業を最小限に抑えたい 概要 AMF(Allied-Telesis Management Framework) とは センターサイトによる複数リモートサイトの一極集中管理によるネットワーク管理 / 運用コスト削減や
主な目的 複数ロケーションのネットワークを一極集中管理したい ネットワーク管理 / 運用機構の集約によりランニングコストを抑制したい 各ロケーションにおける現場メンテナンス / リカバリー作業を最小限に抑えたい 概要 AMF(Allied-Telesis Management Framework) とは センターサイトによる複数リモートサイトの一極集中管理によるネットワーク管理 / 運用コスト削減や
リモートアクセス型L2TP+IPsec VPN 設定例
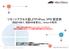 リモートアクセス型 L2TP+IPsec VPN 設定例 ( 既設 FW あり 既設 NW 変更なし Global IP 使用 ) 本資料は 弊社での検証に基づき Firewall AR シリーズ VPN クライアント の操作方法を記載したものです すべての環境での動作を保証するものではありません iphone ipad は Apple Inc. の商標です iphone の商標は アイホン株式会社のライセンスに基づき使用されています
リモートアクセス型 L2TP+IPsec VPN 設定例 ( 既設 FW あり 既設 NW 変更なし Global IP 使用 ) 本資料は 弊社での検証に基づき Firewall AR シリーズ VPN クライアント の操作方法を記載したものです すべての環境での動作を保証するものではありません iphone ipad は Apple Inc. の商標です iphone の商標は アイホン株式会社のライセンスに基づき使用されています
リモートアクセス型L2TP+IPsec VPN
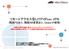 リモートアクセス型 L2TP+IPsec VPN ( 既設 FW あり 既設 NW 変更あり Global IP 使用 ) 本資料は 弊社での検証に基づき Firewall AR シリーズ VPN クライアント の操作方法を記載したものです すべての環境での動作を保証するものではありません iphone ipad は Apple Inc. の商標です iphone の商標は アイホン株式会社のライセンスに基づき使用されています
リモートアクセス型 L2TP+IPsec VPN ( 既設 FW あり 既設 NW 変更あり Global IP 使用 ) 本資料は 弊社での検証に基づき Firewall AR シリーズ VPN クライアント の操作方法を記載したものです すべての環境での動作を保証するものではありません iphone ipad は Apple Inc. の商標です iphone の商標は アイホン株式会社のライセンスに基づき使用されています
目次 1ファームウェアインストーラーについて ファームウェアインストーラーの動作 ダウンロードモジュール ファームウェアインストーラーの動作環境 ファームウェアインストーラーのインストール アンインストール... 4
 別紙 2 サザンクロスルータシステム AR415S バージョンアップ手順書 目次 1ファームウェアインストーラーについて... 3 1.1 ファームウェアインストーラーの動作... 3 1.2 ダウンロードモジュール... 3 1.3 ファームウェアインストーラーの動作環境... 4 2ファームウェアインストーラーのインストール... 4 2.1 アンインストール... 4 3バージョンアップ...
別紙 2 サザンクロスルータシステム AR415S バージョンアップ手順書 目次 1ファームウェアインストーラーについて... 3 1.1 ファームウェアインストーラーの動作... 3 1.2 ダウンロードモジュール... 3 1.3 ファームウェアインストーラーの動作環境... 4 2ファームウェアインストーラーのインストール... 4 2.1 アンインストール... 4 3バージョンアップ...
モバイルWi-FiルーターとARファミリの設定例
 モバイル Wi-Fi ルーターと AR ファミリの設定例 2012/9/4 アライドテレシス株式会社 Copyright 2012 Allied Telesis K.K. All Rights Reserved. 目次 1. 移動体データ通信サービスをデータ通信で利用するメリット 2. VPN ルーターと組み合わせられる移動体通信端末の種類 3. 設定例モバイル Wi-Fi ルーターを用いた VPN
モバイル Wi-Fi ルーターと AR ファミリの設定例 2012/9/4 アライドテレシス株式会社 Copyright 2012 Allied Telesis K.K. All Rights Reserved. 目次 1. 移動体データ通信サービスをデータ通信で利用するメリット 2. VPN ルーターと組み合わせられる移動体通信端末の種類 3. 設定例モバイル Wi-Fi ルーターを用いた VPN
リモートアクセス型L2TP+IPsec VPN
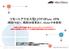 リモートアクセス型 L2TP+IPsec VPN ( 既設 FW あり 既設 NW 変更あり Global IP 未使用 ) 本資料は 弊社での検証に基づき Firewall AR シリーズ VPN クライアント の操作方法を記載したものです すべての環境での動作を保証するものではありません iphone ipad は Apple Inc. の商標です iphone の商標は アイホン株式会社のライセンスに基づき使用されています
リモートアクセス型 L2TP+IPsec VPN ( 既設 FW あり 既設 NW 変更あり Global IP 未使用 ) 本資料は 弊社での検証に基づき Firewall AR シリーズ VPN クライアント の操作方法を記載したものです すべての環境での動作を保証するものではありません iphone ipad は Apple Inc. の商標です iphone の商標は アイホン株式会社のライセンスに基づき使用されています
IPsec RADIUS + ワンタイムパスワード設定例
 Soliton NetAttest EPS + OneTimePassword + AR router series IPsec RADIUS + ワンタイムパスワード設定例 2012/APL アライドテレシス株式会社 Revision 1.0 はじめに 本資料は 弊社での検証に基づき NetAttest EPS 及び AR シリーズ VPN クライアント端末の操作方法を記載したものです すべての環境での動作を保証するものではありません
Soliton NetAttest EPS + OneTimePassword + AR router series IPsec RADIUS + ワンタイムパスワード設定例 2012/APL アライドテレシス株式会社 Revision 1.0 はじめに 本資料は 弊社での検証に基づき NetAttest EPS 及び AR シリーズ VPN クライアント端末の操作方法を記載したものです すべての環境での動作を保証するものではありません
Dynamic VPN Dynamic VPN IPSec VPN PC SRX IPSec VPN SRX PC IPSec 2 Copyright 2010 Juniper Networks, Inc.
 SRX DYNAMIC VPN Dynamic VPN Dynamic VPN IPSec VPN PC SRX IPSec VPN SRX PC IPSec 2 Copyright 2010 Juniper Networks, Inc. www.juniper.net DYNAMIC VPN Netscreen Remote(NS-R) (NS-R) PC SRX Dynamic VPN SRX
SRX DYNAMIC VPN Dynamic VPN Dynamic VPN IPSec VPN PC SRX IPSec VPN SRX PC IPSec 2 Copyright 2010 Juniper Networks, Inc. www.juniper.net DYNAMIC VPN Netscreen Remote(NS-R) (NS-R) PC SRX Dynamic VPN SRX
untitled
 IGMP Snooping... 2... 5... 5 ADD IGMPSNOOPING MCGROUP... 6 DELETE IGMPSNOOPING...... 8 DISABLE IGMPSNOOPING...... 9 ENABLE IGMPSNOOPING...... 10 SET IGMPSNOOPING... 11 SET IGMPSNOOPING MCGROUP... 13 SHOW
IGMP Snooping... 2... 5... 5 ADD IGMPSNOOPING MCGROUP... 6 DELETE IGMPSNOOPING...... 8 DISABLE IGMPSNOOPING...... 9 ENABLE IGMPSNOOPING...... 10 SET IGMPSNOOPING... 11 SET IGMPSNOOPING MCGROUP... 13 SHOW
IP... 2 IP... 2 IP... 2 IP... 2 VLAN... 3 IP ADD IP IPADDRESS... 5 DELETE IP... 7 PING SETIP SHOW IP IP CentreCOM FS9
 ... 2... 2... 2... 2 VLAN... 3... 3... 4... 4 ADD ADDRESS... 5 DELETE... 7 PING.... 8 SET... 10 SHOW... 11 CentreCOM FS900S 1.0.0 1 Internet Protocol 2 Telnet 1. 2. VLAN VLAN default ADD ADDRESS=192.168.10.5
... 2... 2... 2... 2 VLAN... 3... 3... 4... 4 ADD ADDRESS... 5 DELETE... 7 PING.... 8 SET... 10 SHOW... 11 CentreCOM FS900S 1.0.0 1 Internet Protocol 2 Telnet 1. 2. VLAN VLAN default ADD ADDRESS=192.168.10.5
RTX1210 取扱説明書
 1 2 3 4 5 1 2 3 4 5 1 2 3 4 5 6 1 2 3 4 5 6 7 8 9 0 A B 6 7 8 9 10 11 show config 12 13 14 15 16 1 2 LAN1 3 4 LAN2 LINK/ DATA SPEED CONSOLE L1/B1 B2 microsd USB DOWN LOAD POWER ALARM STATUS 5 6 7 8 LAN3
1 2 3 4 5 1 2 3 4 5 1 2 3 4 5 6 1 2 3 4 5 6 7 8 9 0 A B 6 7 8 9 10 11 show config 12 13 14 15 16 1 2 LAN1 3 4 LAN2 LINK/ DATA SPEED CONSOLE L1/B1 B2 microsd USB DOWN LOAD POWER ALARM STATUS 5 6 7 8 LAN3
VLAN.dvi
 ... 2... 2.... 2... 3... 5... 7... 9... 9 ADD BRIDGE... 10 ADD PORT... 11 CREATE..... 13 DELETE BRIDGE... 14 DELETE PORT... 15 DESTROY.... 16 SET BRIDGE... 17 SET PORT.... 18 SHOW...... 19 SHOW BRIDGE...
... 2... 2.... 2... 3... 5... 7... 9... 9 ADD BRIDGE... 10 ADD PORT... 11 CREATE..... 13 DELETE BRIDGE... 14 DELETE PORT... 15 DESTROY.... 16 SET BRIDGE... 17 SET PORT.... 18 SHOW...... 19 SHOW BRIDGE...
00.目次_ope
 816XL ii iii iv iv User Entry 1 3 v vi vii viii 1 1 C: >VTTERM 1- 1 1-3 1 1-4 1 1-5 1 1-6 1 1-7 1 1-8 1 1-9 1 1-10 C: >VTN 1 Host Name: 1-11 1 01 1-1 0.0.0.0 1 1-13 1 1-14 - -3 Port status and configuration
816XL ii iii iv iv User Entry 1 3 v vi vii viii 1 1 C: >VTTERM 1- 1 1-3 1 1-4 1 1-5 1 1-6 1 1-7 1 1-8 1 1-9 1 1-10 C: >VTN 1 Host Name: 1-11 1 01 1-1 0.0.0.0 1 1-13 1 1-14 - -3 Port status and configuration
MLDS.dvi
 ... 2... 5... 5 ADD MLDSNOOPING VLAN.... 6 CREATE MLDSNOOPING VLAN... 8 DELETE MLDSNOOPING VLAN... 9 DISABLE MLDSNOOPING...... 11 ENABLE MLDSNOOPING...... 12 SET MLDSNOOPING TIMEOUT... 13 SET MLDSNOOPING
... 2... 5... 5 ADD MLDSNOOPING VLAN.... 6 CREATE MLDSNOOPING VLAN... 8 DELETE MLDSNOOPING VLAN... 9 DISABLE MLDSNOOPING...... 11 ENABLE MLDSNOOPING...... 12 SET MLDSNOOPING TIMEOUT... 13 SET MLDSNOOPING
NS-3510イーサネットアクセスデバイス取扱説明書-02
 NS-3510 2 3 4 CONSOLE test CONSOLE test ROM BOOT... Hit [Enter] key to enter ROM-Monitor... 1st Boot : 1000000 2nd Boot : 1000200
NS-3510 2 3 4 CONSOLE test CONSOLE test ROM BOOT... Hit [Enter] key to enter ROM-Monitor... 1st Boot : 1000000 2nd Boot : 1000200
IGMPS.dvi
 ... 2... 5... 5 ADD IGMPSNOOPING... 6 DELETE IGMPSNOOPING...... 8 DISABLE IGMPSNOOPING...... 9 ENABLE IGMPSNOOPING...... 10 SET IGMPSNOOPING TIMEOUT... 11 SHOW IGMPSNOOPING... 12 CentreCOM FS900M 1.6.0
... 2... 5... 5 ADD IGMPSNOOPING... 6 DELETE IGMPSNOOPING...... 8 DISABLE IGMPSNOOPING...... 9 ENABLE IGMPSNOOPING...... 10 SET IGMPSNOOPING TIMEOUT... 11 SHOW IGMPSNOOPING... 12 CentreCOM FS900M 1.6.0
WEB.dvi
 ... 5... 5... 5... 7... 8... 8... 10... 11... 11... 12... 13 HTTP... 13... 14... 15... 15... 15 IP... 15... 16... 17... 18 NTP... 18 SNMP.... 19 SNMP... 19 SNMP... 20 SNMP... 22 SNMP... 22... 22... 23...
... 5... 5... 5... 7... 8... 8... 10... 11... 11... 12... 13 HTTP... 13... 14... 15... 15... 15 IP... 15... 16... 17... 18 NTP... 18 SNMP.... 19 SNMP... 19 SNMP... 20 SNMP... 22 SNMP... 22... 22... 23...
リング型IPカメラ監視ソリューション(マルチキャスト編)
 CentreCOM x900 IP IP ( ) IP surveillance Solution 01 SNMP Manager Syslog Server NTP Server x900-24xt_2 Link Aggregation x900-24xt_1 FS926M-PS_1 FS926M-PS_2 x600-24ts EPSR (Ethernet Protected Switched Ring)
CentreCOM x900 IP IP ( ) IP surveillance Solution 01 SNMP Manager Syslog Server NTP Server x900-24xt_2 Link Aggregation x900-24xt_1 FS926M-PS_1 FS926M-PS_2 x600-24ts EPSR (Ethernet Protected Switched Ring)
RouteMagic Controller RMC-MP200 / MP Version
 RouteMagic Controller RMC-MP200 / MP1200 - Version 3.7.1 - RouteMagic Controller( RMC ) 3.7 RMC RouteMagic RouteMagic Controller RouteMagic Controller MP1200 / MP200 Version 3.7 RouteMagic Controller Version
RouteMagic Controller RMC-MP200 / MP1200 - Version 3.7.1 - RouteMagic Controller( RMC ) 3.7 RMC RouteMagic RouteMagic Controller RouteMagic Controller MP1200 / MP200 Version 3.7 RouteMagic Controller Version
IPSEC-VPN IPsec(Security Architecture for Internet Protocol) IP SA(Security Association, ) SA IKE IKE 1 1 ISAKMP SA( ) IKE 2 2 IPSec SA( 1 ) IPs
 IPSEC VPN IPSEC-VPN IPsec(Security Architecture for Internet Protocol) IP SA(Security Association, ) SA IKE 1 2 2 IKE 1 1 ISAKMP SA( ) IKE 2 2 IPSec SA( 1 ) IPsec SA IKE Initiator Responder IPsec-VPN ISAKMP
IPSEC VPN IPSEC-VPN IPsec(Security Architecture for Internet Protocol) IP SA(Security Association, ) SA IKE 1 2 2 IKE 1 1 ISAKMP SA( ) IKE 2 2 IPSec SA( 1 ) IPsec SA IKE Initiator Responder IPsec-VPN ISAKMP
RouteMagic Controller( RMC ) 3.6 RMC RouteMagic RouteMagic Controller RouteMagic Controller MP1200 / MP200 Version 3.6 RouteMagic Controller Version 3
 RouteMagic Controller RMC-MP200 / MP1200 - Version 3.6 - RouteMagic Controller( RMC ) 3.6 RMC RouteMagic RouteMagic Controller RouteMagic Controller MP1200 / MP200 Version 3.6 RouteMagic Controller Version
RouteMagic Controller RMC-MP200 / MP1200 - Version 3.6 - RouteMagic Controller( RMC ) 3.6 RMC RouteMagic RouteMagic Controller RouteMagic Controller MP1200 / MP200 Version 3.6 RouteMagic Controller Version
untitled
 FutureNet Microsoft Corporation Microsoft Windows Windows 95 Windows 98 Windows NT4.0 Windows 2000, Windows XP, Microsoft Internet Exproler (1) (2) (3) COM. (4) (5) ii ... 1 1.1... 1 1.2... 3 1.3... 6...
FutureNet Microsoft Corporation Microsoft Windows Windows 95 Windows 98 Windows NT4.0 Windows 2000, Windows XP, Microsoft Internet Exproler (1) (2) (3) COM. (4) (5) ii ... 1 1.1... 1 1.2... 3 1.3... 6...
SRT100 コマンド設定運用説明書
 8 9 46 2 ...2 SRT100...4...6...8...9...9...10...11...12...14...15...19 CONSOLE...20 1....20 2.CONSOLE...21 3.CONSOLE...22...24 1....24 2....25 3....25 4....26 5....26 6.syslog...27 7.LAN...28 8.WAN...28
8 9 46 2 ...2 SRT100...4...6...8...9...9...10...11...12...14...15...19 CONSOLE...20 1....20 2.CONSOLE...21 3.CONSOLE...22...24 1....24 2....25 3....25 4....26 5....26 6.syslog...27 7.LAN...28 8.WAN...28
Win XP SP3 Japanese Ed. NCP IPSec client Hub L3 SW SRX100 Policy base VPN fe-0/0/0 vlan.0 Win 2003 SVR /
 SRX dial-up VPN (NCP ) Win XP SP3 Japanese Ed. NCP IPSec client Hub L3 SW SRX100 Policy base VPN fe-0/0/0 vlan.0 Win 2003 SVR.216 172.27.24.0/24.254.254.1.1.100 100.100.100.0/24 192.168.1.0/24 Test devices
SRX dial-up VPN (NCP ) Win XP SP3 Japanese Ed. NCP IPSec client Hub L3 SW SRX100 Policy base VPN fe-0/0/0 vlan.0 Win 2003 SVR.216 172.27.24.0/24.254.254.1.1.100 100.100.100.0/24 192.168.1.0/24 Test devices
Jlspec
 1OFF 通常 OFF 通常 2 ON 設定内容の初期化を行う ( 工場出荷状態 ) OFF 通常 3 ON 自己診断 / 設定内容の印字を行う 4OFF 通常 %!PS-Adobe-2.0 /Courier findfont 10 scalefont setfont /LEFT 36 def /TOP 792 def /PITCH 12 def /LF {show /x LEFT def /y
1OFF 通常 OFF 通常 2 ON 設定内容の初期化を行う ( 工場出荷状態 ) OFF 通常 3 ON 自己診断 / 設定内容の印字を行う 4OFF 通常 %!PS-Adobe-2.0 /Courier findfont 10 scalefont setfont /LEFT 36 def /TOP 792 def /PITCH 12 def /LF {show /x LEFT def /y
IP... 9 IP... 9 IP IP IP Unnumbered IP PPP IPCP IP DHCP IP IP
 ... 9... 9... 9... 10... 11... 17... 23... 25... 25... 25 Unnumbered... 26 PPP CP... 26 DHCP... 27... 28... 28... 30... 30... 31... 33 R... 36... 36 R Version1 2... 36... 36 R... 38 OSPF... 40... 40 AS
... 9... 9... 9... 10... 11... 17... 23... 25... 25... 25 Unnumbered... 26 PPP CP... 26 DHCP... 27... 28... 28... 30... 30... 31... 33 R... 36... 36 R Version1 2... 36... 36 R... 38 OSPF... 40... 40 AS
Si-R30コマンドリファレンス
 8 8.1 SNMP ( ) 8.1.1 snmp service ( ) SNMP SNMP snmp service on SNMP SNMP off SNMP SNMP SNMP SNMP Si-R30 SNMP snmp service off 171 8.1.2 snmp agent contact ( ) SNMP snmp agent contact []
8 8.1 SNMP ( ) 8.1.1 snmp service ( ) SNMP SNMP snmp service on SNMP SNMP off SNMP SNMP SNMP SNMP Si-R30 SNMP snmp service off 171 8.1.2 snmp agent contact ( ) SNMP snmp agent contact []
アライドテレシス ディストリビューションスイッチ x610シリーズで実現するVRF-Lite + Tagging + EPSR for x610
 主な目的 IP アドレスが重複した環境を統合したい 各ネットワークのセキュリティを確保したい 運用効率化を図りたい 概要 自治体合併など 個別に稼動していたネットワークを統合する際の課題の一つに IP アドレス体系やネットワークポリシーの見直しがあります しかし IP アドレスを変更することは統合作業の煩雑化やシステムの見直しなど容易ではありません そこで 暫定的にも恒久的にも利用できる VRF-Lite
主な目的 IP アドレスが重複した環境を統合したい 各ネットワークのセキュリティを確保したい 運用効率化を図りたい 概要 自治体合併など 個別に稼動していたネットワークを統合する際の課題の一つに IP アドレス体系やネットワークポリシーの見直しがあります しかし IP アドレスを変更することは統合作業の煩雑化やシステムの見直しなど容易ではありません そこで 暫定的にも恒久的にも利用できる VRF-Lite
GA-1190J
 GA-1190J 1 1. 2. 3. 4. 2 5. 3 PDF 4 PDF PDF PDF PDF PDF PDF PDF PDF 5 6 ...1...2...4 1...12 2...16...18 3...22 PCL/PS...23 4...26 5...30 ETHERNET...31 TCP/IP...33 IPX/SPX...38 AppleTalk...40 HTTP...42
GA-1190J 1 1. 2. 3. 4. 2 5. 3 PDF 4 PDF PDF PDF PDF PDF PDF PDF PDF 5 6 ...1...2...4 1...12 2...16...18 3...22 PCL/PS...23 4...26 5...30 ETHERNET...31 TCP/IP...33 IPX/SPX...38 AppleTalk...40 HTTP...42
設定手順
 IP Cluster & Check Point NGX (IPSO 4.0 & Check Point NGX (R60)) 2007 7 IP Cluster & Check Point NGX...2 1 Gateway Cluster...6 1-1 cpconfig...6 1-2 Gateway Cluster...6 1-3 3rd Party Configuration...8 1-4
IP Cluster & Check Point NGX (IPSO 4.0 & Check Point NGX (R60)) 2007 7 IP Cluster & Check Point NGX...2 1 Gateway Cluster...6 1-1 cpconfig...6 1-2 Gateway Cluster...6 1-3 3rd Party Configuration...8 1-4
SRX IDP Full IDP Stateful Inspection 8 Detection mechanisms including Stateful Signatures and Protocol Anomalies Reassemble, normalize, eliminate ambi
 IDP (INTRUSION DETECTION AND PREVENTION) SRX IDP Full IDP Stateful Inspection 8 Detection mechanisms including Stateful Signatures and Protocol Anomalies Reassemble, normalize, eliminate ambiguity Track
IDP (INTRUSION DETECTION AND PREVENTION) SRX IDP Full IDP Stateful Inspection 8 Detection mechanisms including Stateful Signatures and Protocol Anomalies Reassemble, normalize, eliminate ambiguity Track
帯域を測ってみよう (適応型QoS/QoS連携/帯域検出機能)
 RTX1100 client server network service ( ) RTX3000 ( ) RTX1500 2 Sound Network Division, YAMAHA 3 Sound Network Division, YAMAHA 172.16.1.100/24 172.16.2.100/24 LAN2 LAN3 RTX1500 RTX1100 client 172.16.1.1/24
RTX1100 client server network service ( ) RTX3000 ( ) RTX1500 2 Sound Network Division, YAMAHA 3 Sound Network Division, YAMAHA 172.16.1.100/24 172.16.2.100/24 LAN2 LAN3 RTX1500 RTX1100 client 172.16.1.1/24
Teradici Corporation #101-4621 Canada Way, Burnaby, BC V5G 4X8 Canada p +1 604 451 5800 f +1 604 451 5818 www.teradici.com Teradici Corporation Teradi
 PCoIP TER0806003 TER0806003 Issue 2 0 Teradici Corporation #101-4621 Canada Way, Burnaby, BC V5G 4X8 Canada p +1 604 451 5800 f +1 604 451 5818 www.teradici.com Teradici Corporation Teradici Teradici Teradici
PCoIP TER0806003 TER0806003 Issue 2 0 Teradici Corporation #101-4621 Canada Way, Burnaby, BC V5G 4X8 Canada p +1 604 451 5800 f +1 604 451 5818 www.teradici.com Teradici Corporation Teradici Teradici Teradici
Agenda IPv4 over IPv6 MAP MAP IPv4 over IPv6 MAP packet MAP Protocol MAP domain MAP domain ASAMAP ASAMAP 2
 MAP Tutorial @ 1 Agenda IPv4 over IPv6 MAP MAP IPv4 over IPv6 MAP packet MAP Protocol MAP domain MAP domain ASAMAP ASAMAP 2 IPv4 over IPv6 IPv6 network IPv4 service Internet Service ProviderISP IPv4 service
MAP Tutorial @ 1 Agenda IPv4 over IPv6 MAP MAP IPv4 over IPv6 MAP packet MAP Protocol MAP domain MAP domain ASAMAP ASAMAP 2 IPv4 over IPv6 IPv6 network IPv4 service Internet Service ProviderISP IPv4 service
SR-X526R1 サーバ収容スイッチ ご利用にあたって
 SR-X526R1 P3NK-3432-05Z0 526R1 V01 SR-X526R1 V01 2009 10 2010 4 2 2011 5 3 2012 3 4 2012 11 5 Microsoft Corporation Copyright FUJITSU LIMITED 2009-2012 2 SR-X526R1 V01...2...5...5...5...5...6...7...8...8...11...11...11...11...11...11...12...12...12...12...13...13...13
SR-X526R1 P3NK-3432-05Z0 526R1 V01 SR-X526R1 V01 2009 10 2010 4 2 2011 5 3 2012 3 4 2012 11 5 Microsoft Corporation Copyright FUJITSU LIMITED 2009-2012 2 SR-X526R1 V01...2...5...5...5...5...6...7...8...8...11...11...11...11...11...11...12...12...12...12...13...13...13
2
 WJ-HD150 Digital Disk Recorder WJ-HD150 2 3 q w e r t y u 4 5 6 7 8 9 10 11 12 13 14 15 16 q w SIGNAL GND AC IN 17 SUNDAY MONDAY TUESDAY WEDNESDAY THURSDAY FRIDAY SATURDAY DAILY Program 1 Event No.1 Event
WJ-HD150 Digital Disk Recorder WJ-HD150 2 3 q w e r t y u 4 5 6 7 8 9 10 11 12 13 14 15 16 q w SIGNAL GND AC IN 17 SUNDAY MONDAY TUESDAY WEDNESDAY THURSDAY FRIDAY SATURDAY DAILY Program 1 Event No.1 Event
リモートアクセス型L2TP+IPsec VPN 設定例
 リモートアクセス型 L2TP+IPsec VPN 設定例 ( 既設 FW あり 既設 NW 変更なし Global IP 未使用 ) 本資料は 弊社での検証に基づき Firewall AR シリーズ RADIUS サーバー VPN クライアント の操作方法を記載したものです すべての環境での動作を保証するものではありません iphone ipad は Apple Inc. の商標です iphone
リモートアクセス型 L2TP+IPsec VPN 設定例 ( 既設 FW あり 既設 NW 変更なし Global IP 未使用 ) 本資料は 弊社での検証に基づき Firewall AR シリーズ RADIUS サーバー VPN クライアント の操作方法を記載したものです すべての環境での動作を保証するものではありません iphone ipad は Apple Inc. の商標です iphone
DICOM UG_JPN_P book
 DICOM 1 2 FUJIFILM SonoSite, Inc. DICOM PACS MPPS DICOM Storage Commitment 3 Locations Devices イーサネットを使用して LAN に接続する方法 M-Turbo MDSm 転送モードを設定する方法 1 Connectivity (Transfer Mode DICOM 2 Yes Locations Archivers
DICOM 1 2 FUJIFILM SonoSite, Inc. DICOM PACS MPPS DICOM Storage Commitment 3 Locations Devices イーサネットを使用して LAN に接続する方法 M-Turbo MDSm 転送モードを設定する方法 1 Connectivity (Transfer Mode DICOM 2 Yes Locations Archivers
1 138
 5 1 2 3 4 5 6 7 8 1 138 BIOS Setup Utility MainAdvancedSecurityPowerExit Setup Warning Item Specific Help Setting items on this menu to incorrect values may cause your system to malfunction. Select 'Yes'
5 1 2 3 4 5 6 7 8 1 138 BIOS Setup Utility MainAdvancedSecurityPowerExit Setup Warning Item Specific Help Setting items on this menu to incorrect values may cause your system to malfunction. Select 'Yes'
スライド 1
 ITCAIP Phone Ver 1.7 2 1. 1 1. 1-1. 1-2. ITCA-IP Phone 1-2-1. 1-2-2. IP 1-2-3. ISP 1-2-4. 1-2-5. HP 1-2-6. ITCA-IP Phone 1-3. 1-3-1. 1-3-2. 1-4. 1-4-1. 1-4-2. 1-4-3. 1-5. 1-5-1. ITCA-IP Phone VoIP 1-5-2.
ITCAIP Phone Ver 1.7 2 1. 1 1. 1-1. 1-2. ITCA-IP Phone 1-2-1. 1-2-2. IP 1-2-3. ISP 1-2-4. 1-2-5. HP 1-2-6. ITCA-IP Phone 1-3. 1-3-1. 1-3-2. 1-4. 1-4-1. 1-4-2. 1-4-3. 1-5. 1-5-1. ITCA-IP Phone VoIP 1-5-2.
SRX License
 SRX ライセンスキー投入手順 株式会社日立ソリューションズネットワークビジネス部セキュリティグループ リビジョン 4.0 初版 2010/05/30 最新版 2012/12/27 Hitachi Solutions, Ltd. 2010-2012. All rights reserved. SRX ライセンスキー投入手順 Contents 1. ライセンスキーの自動インポート ( インターネット接続必須
SRX ライセンスキー投入手順 株式会社日立ソリューションズネットワークビジネス部セキュリティグループ リビジョン 4.0 初版 2010/05/30 最新版 2012/12/27 Hitachi Solutions, Ltd. 2010-2012. All rights reserved. SRX ライセンスキー投入手順 Contents 1. ライセンスキーの自動インポート ( インターネット接続必須
IOS ゾーン ベースのポリシー ファイアウォールを使用した IOS ルータでの AnyConnect VPN クライアントの設定例
 IOS ゾーンベースのポリシーファイアウォールを使用した IOS ルータでの AnyConnect VPN クライアントの設定例 目次 はじめに前提条件要件使用するコンポーネント表記法設定ネットワーク図 Cisco IOS AnyConnect サーバの設定確認トラブルシューティングトラブルシューティングのためのコマンド関連情報 はじめに Cisco IOS ソフトウェアリリース 12.4(20)T
IOS ゾーンベースのポリシーファイアウォールを使用した IOS ルータでの AnyConnect VPN クライアントの設定例 目次 はじめに前提条件要件使用するコンポーネント表記法設定ネットワーク図 Cisco IOS AnyConnect サーバの設定確認トラブルシューティングトラブルシューティングのためのコマンド関連情報 はじめに Cisco IOS ソフトウェアリリース 12.4(20)T
RouteMagic Controller RMC-MP200 / MP Version
 RouteMagic Controller RMC-MP200 / MP1200 - Version 3.5.2 - RouteMagic Controller( RMC ) 3.5.2 RMC RouteMagic RouteMagic Controller RouteMagic Controller MP1200 / MP200 Version 3.5 RouteMagic Controller
RouteMagic Controller RMC-MP200 / MP1200 - Version 3.5.2 - RouteMagic Controller( RMC ) 3.5.2 RMC RouteMagic RouteMagic Controller RouteMagic Controller MP1200 / MP200 Version 3.5 RouteMagic Controller
Si-R180 ご利用にあたって
 P3NK-2472-01Z0 GeoStream Si-R 180 LAN 2007 7 Microsoft Corporation All rights reserved, Copyright 2007 2 ...2...5...5...5...5...6...7...8...8...11...11 LAN...11...11...12...12...12...12...12...13 ISO/IEC15408...14
P3NK-2472-01Z0 GeoStream Si-R 180 LAN 2007 7 Microsoft Corporation All rights reserved, Copyright 2007 2 ...2...5...5...5...5...6...7...8...8...11...11 LAN...11...11...12...12...12...12...12...13 ISO/IEC15408...14
fx-9860G Manager PLUS_J
 fx-9860g J fx-9860g Manager PLUS http://edu.casio.jp k 1 k III 2 3 1. 2. 4 3. 4. 5 1. 2. 3. 4. 5. 1. 6 7 k 8 k 9 k 10 k 11 k k k 12 k k k 1 2 3 4 5 6 1 2 3 4 5 6 13 k 1 2 3 1 2 3 1 2 3 1 2 3 14 k a j.+-(),m1
fx-9860g J fx-9860g Manager PLUS http://edu.casio.jp k 1 k III 2 3 1. 2. 4 3. 4. 5 1. 2. 3. 4. 5. 1. 6 7 k 8 k 9 k 10 k 11 k k k 12 k k k 1 2 3 4 5 6 1 2 3 4 5 6 13 k 1 2 3 1 2 3 1 2 3 1 2 3 14 k a j.+-(),m1
MR1000 コマンド設定事例集
 V21 LAN 2005 1 2005 3 2 Microsoft Corporation OMRON Corporation 2004-2005 All Rights Reserved. 2 V21... 2... 6... 6... 6... 6 1... 7 1.1 LAN... 8 1.2 CATV... 10 1.3 LAN... 12 1.4 IPv4 IPv6... 14 1.5...
V21 LAN 2005 1 2005 3 2 Microsoft Corporation OMRON Corporation 2004-2005 All Rights Reserved. 2 V21... 2... 6... 6... 6... 6 1... 7 1.1 LAN... 8 1.2 CATV... 10 1.3 LAN... 12 1.4 IPv4 IPv6... 14 1.5...
DocuWide 2051/2051MF 補足説明書
 ëêèõ . 2 3 4 5 6 7 8 9 0 2 3 4 [PLOTTER CONFIGURATION] [DocuWide 2050/205 Version 2.2.0] [SERIAL] BAUD_RATE =9600 DATA_BIT =7 STOP_BIT = PARITY =EVEN HANDSHAKE =XON/XOFF EOP_TIMEOUT_VALUE =0 OUTPUT RESPONSE
ëêèõ . 2 3 4 5 6 7 8 9 0 2 3 4 [PLOTTER CONFIGURATION] [DocuWide 2050/205 Version 2.2.0] [SERIAL] BAUD_RATE =9600 DATA_BIT =7 STOP_BIT = PARITY =EVEN HANDSHAKE =XON/XOFF EOP_TIMEOUT_VALUE =0 OUTPUT RESPONSE
2 BIG-IP 800 LTM v HF2 V LTM L L L IP GUI VLAN.
 BIG-IP800 LTM v11.4.0 HF2 V1.0 F5 Networks Japan 2 BIG-IP 800 LTM v11.4.0 HF2 V1.0...1 1....3 1.1. LTM...3 2. L3...4 2.1. L3...4 2.2. L3...5 3....6 3.1....6 3.1.1. IP...6 3.1.2. GUI...10 3.1.3. VLAN...19
BIG-IP800 LTM v11.4.0 HF2 V1.0 F5 Networks Japan 2 BIG-IP 800 LTM v11.4.0 HF2 V1.0...1 1....3 1.1. LTM...3 2. L3...4 2.1. L3...4 2.2. L3...5 3....6 3.1....6 3.1.1. IP...6 3.1.2. GUI...10 3.1.3. VLAN...19
ES1018V2_24V2_MG.book
 2009 6 Management Ver.2.0 Guide ES1018V2 ES1024V2 ES1018V2 ES1024V2 1.05.06 1....1 1.1... 2 1.2 CLI... 3 1.2.1?... 3 1.2.2 Default... 3 1.2.3 Help... 3 1.2.4 Logout... 3 1.2.5 Ping... 3 1.2.6 Reset...
2009 6 Management Ver.2.0 Guide ES1018V2 ES1024V2 ES1018V2 ES1024V2 1.05.06 1....1 1.1... 2 1.2 CLI... 3 1.2.1?... 3 1.2.2 Default... 3 1.2.3 Help... 3 1.2.4 Logout... 3 1.2.5 Ping... 3 1.2.6 Reset...
AMF Cloud ソリューション
 アライドテレシス バーチャルAMFアプライアンスで実現する 主な目的 複数の拠点間を繋ぐ大規模なネットワークを構築したい AMFコントローラー/マスターを仮想マシン上に集約したい AMF機能を活用したネットワーク全体の一元管理を行い 運用コストを削減したい 概要 これまで AMF機能を用いることで ネットワークの一元管理が可能となり 機器故障時 には代替機と差し替えるだけで自動的に復旧させるAuto
アライドテレシス バーチャルAMFアプライアンスで実現する 主な目的 複数の拠点間を繋ぐ大規模なネットワークを構築したい AMFコントローラー/マスターを仮想マシン上に集約したい AMF機能を活用したネットワーク全体の一元管理を行い 運用コストを削減したい 概要 これまで AMF機能を用いることで ネットワークの一元管理が可能となり 機器故障時 には代替機と差し替えるだけで自動的に復旧させるAuto
Cisco Umbrella Branch Cisco Umbrella Branch Cisco ISR Umbrella Branch
 Cisco Umbrella Branch Cisco Umbrella Branch Cisco ISR 4000 1 2 3 Umbrella Branch 1 Cisco Umbrella Branch Cisco ISR 4000 Cisco Umbrella Branch Security K9 ROM Monitor (ROMMON) 16.2(1r) ROMMON 16.2(1r) 3
Cisco Umbrella Branch Cisco Umbrella Branch Cisco ISR 4000 1 2 3 Umbrella Branch 1 Cisco Umbrella Branch Cisco ISR 4000 Cisco Umbrella Branch Security K9 ROM Monitor (ROMMON) 16.2(1r) ROMMON 16.2(1r) 3
FutureNet CS-SEILシリーズ コマンドリファレンス ver.1.82対応版
 FutureNet CS-SEIL Series CS-SEIL-510/C CS-SEIL/Turbo Firmware Version 1.82 FutureNet CS-SEIL.............................................. 1 1............................................. 11 1.1.........................................
FutureNet CS-SEIL Series CS-SEIL-510/C CS-SEIL/Turbo Firmware Version 1.82 FutureNet CS-SEIL.............................................. 1 1............................................. 11 1.1.........................................
ヤマハ ルーター ファイアウォール機能~説明資料~
 1 RT140i #1(PPP) RT105i RTA52i R (PP#) (LAN#) [NAT] R LAN LAN 2 #2() RT300i RTW65b RT140e RT105e (LAN2) R (LAN1) RTA55i R LAN LAN 3 #3(PPPoE) R (LAN#) (PP#) (PP#) LAN ISDN/ LAN 4 RT300i RT105 #4(VPN) R
1 RT140i #1(PPP) RT105i RTA52i R (PP#) (LAN#) [NAT] R LAN LAN 2 #2() RT300i RTW65b RT140e RT105e (LAN2) R (LAN1) RTA55i R LAN LAN 3 #3(PPPoE) R (LAN#) (PP#) (PP#) LAN ISDN/ LAN 4 RT300i RT105 #4(VPN) R
SR-X324T1/316T1 サーバ収容スイッチ ご利用にあたって
 SR-X324T1/316T1 P3NK-4092-04Z0 324T1/316T1 V01 SR-X324T1/316T1 V01 2010 4 2011 5 2 2012 3 3 2012 11 4 Microsoft Corporation Copyright FUJITSU LIMITED 2010-2012 2 SR-X324T1/316T1 V01...2...5...5...5...5...6...7...8...8...11...11...11...11...11...11...12...12...12...12...12...13...13
SR-X324T1/316T1 P3NK-4092-04Z0 324T1/316T1 V01 SR-X324T1/316T1 V01 2010 4 2011 5 2 2012 3 3 2012 11 4 Microsoft Corporation Copyright FUJITSU LIMITED 2010-2012 2 SR-X324T1/316T1 V01...2...5...5...5...5...6...7...8...8...11...11...11...11...11...11...12...12...12...12...12...13...13
HA8000シリーズ ユーザーズガイド ~BIOS編~ HA8000/RS110/TS10 2013年6月~モデル
 P1E1M01500-3 - - - LSI MegaRAID SAS-MFI BIOS Version x.xx.xx (Build xxxx xx, xxxx) Copyright (c) xxxx LSI Corporation HA -0 (Bus xx Dev
P1E1M01500-3 - - - LSI MegaRAID SAS-MFI BIOS Version x.xx.xx (Build xxxx xx, xxxx) Copyright (c) xxxx LSI Corporation HA -0 (Bus xx Dev
CentreCOM FS909M/FS917M/FS926M 取扱説明書
 FS909M FS917M FS926M FS909M FS917M FS926M 4 5 6 7 8 9 10 11 12 1 14 FS909M FS917M FS926M FS909M/FS917MFS926M FS909M/FS917M FS926M FS909M/FS917M FS926M FS926M 15 16 17 18 19 20 21 22 23 24 2 26 FS909M/FS917M
FS909M FS917M FS926M FS909M FS917M FS926M 4 5 6 7 8 9 10 11 12 1 14 FS909M FS917M FS926M FS909M/FS917MFS926M FS909M/FS917M FS926M FS909M/FS917M FS926M FS926M 15 16 17 18 19 20 21 22 23 24 2 26 FS909M/FS917M
Cisco Aironet 1130AG アクセス ポイント クイック スタート ガイド
 CONTENTS 1 IP 2 3 6 7 9 12 15 17 18 IP 20 CLI IP 21 Telnet CLI 23 24 28 802.11G 802.11A 34 38 Express Security 40 Express Security 41 SSID 42 47 LED 48 50 SSID50 WEP 50 51 52 MODE 52 Web 53 55 1 56 IP
CONTENTS 1 IP 2 3 6 7 9 12 15 17 18 IP 20 CLI IP 21 Telnet CLI 23 24 28 802.11G 802.11A 34 38 Express Security 40 Express Security 41 SSID 42 47 LED 48 50 SSID50 WEP 50 51 52 MODE 52 Web 53 55 1 56 IP
AMFマルチテナントソリューション
 主な目的 複数の拠点間を繋ぐ大規模なネットワークを構築したい AMFコントローラー / マスターを仮想マシン上に集約したい AMF 機能を活用したネットワーク全体の一元管理を行い 運用コストを削減したい 複数テナントがそれぞれ独立して動作し かつ上位のコントローラーから複数テナントを集中管理可能なAMFネットワークを構築したい 概要 AMF を使用することで ネットワークデバイスの一元管理や自動復旧
主な目的 複数の拠点間を繋ぐ大規模なネットワークを構築したい AMFコントローラー / マスターを仮想マシン上に集約したい AMF 機能を活用したネットワーク全体の一元管理を行い 運用コストを削減したい 複数テナントがそれぞれ独立して動作し かつ上位のコントローラーから複数テナントを集中管理可能なAMFネットワークを構築したい 概要 AMF を使用することで ネットワークデバイスの一元管理や自動復旧
